- INFORMATION TECHNOLOGY 200910
- ..Jasmeet Chap 01 Intro To Computers
- ..Bliana Chap 02 Internet
- ..Adeyinka Chap 03 Application Software
- ..Pramilah Chap 04 System Unit
- ..Mahendran Chap 06 Output
- ..Faizan Chap 07 Storage
- ..Amr Chap 08 Operating Systems & Utility Programs...
- ..Dennis Chap 09 Data Communication
- ..Gevita Chap 10 Database Management
- ..Chen-special-topic-01-Multimedia
- ..Wong Pau Tung-special-topic-02-Virus
Thursday, December 17, 2009
INFORMATION TECHNOLOGY 200910
Find the file in Google Groups

..Jasmeet Chap 01 Intro To Computers
Find the file in Google Groups

Jasmeet Chap 01 Intro To Computers - Presentation Transcript
CHAPTER 1
INTRODUCTION TO COMPUTERS
By : Jasmeet Khosa
What is a computer ?
How is computer defined ?
Electronic device operating under the control of instructions stored in its own memory
Accepts Data
Processes Data into Information
Produces and stores results
What is a computer ?
What is the information processing cycle ?
Input
Process
Output
Storage
Communication
The components of a computer ?
What is an input device ?
Hardware used to enter data and instructions.
What is and output device ?
Hardware that conveys information to one or more people.
What is a system Unit ?
Case containing electronic components used to process data.
The components of a computer ?
What are the two main components on the motherboard ?
Central Processing Unit (CPU)
* Also called as processor.
Memory
The components of a computer ?
What is storage?
Holds Data, instructions and information for future use.
The two components of storage are:
Storage Media
Storage Device
The components of a computer ?
Examples of storage media are:
Portable, thin memory cards
USB flash drive
Floppy Disk
Compact Disk
(CD)
Hard Disk
The components of a computer ?
What is a communications device ?
Hardware components that enables a computer to send and receive Data, instructions, and information.
Occurs over cables, telephone lines, cellular radio network, Satellites, and others transmission media.
ADVANTAGES AND DISADVANTAGES OF USING COMPUTERS ?
What is the advantages of using computers ?
Reliability
Speed
Communications
Consistency
Storage
ADVANTAGES AND DISADVANTAGES OF USING COMPUTERS ?
What is the disadvantages of using computers ?
Violation of privacy
Impact on Labor Force
Health Risks
Impact on Environment
Network and the internet ?
What is a network ?
Collection of computers and devices connected together.
Communications Device
Transmission Media
Enable a connection between computers
Cables
Satellites
Telephone lines
Cellular radio
One type is a modem
Network and the internet ?
To save time and money
What are the reasons to internet ?
To share
Resources
Information
Hardware devices
Data
Software programs
Network and the internet ?
Why do users access the internet ?
Communication
Information
Shopping
Banking and investing
Classes
Entertainment
COMPUTER SOFTWARE?
What is a software ?
Consists of a series of instructions that tells the computer what to do
Also called a program
COMPUTER SOFTWARE?
What is system software ?
Programs that control or maintain the operations of the computer and its devices.
What is application software ?
Programs that performs that perform specific tasks for users.
What is a programmers ?
Someone who develops applications or system software.
Categories of computers ?
What are the categories of computers ?
Microcomputers
Mobile computers and mobile devices
Midrange Servers
Mainframes
Supercomputers
Embedded Computers
Categories of computers ?
What are the categories of computers ?
Under microcomputers there are :
Desktop
Laptop
Tablet Pc
Palm PC
PDA
Net book
SERVERS?
What types of servers are there ?
Midrange server
Powerful, large computer that supports up to a few thousand computer.
Mainframe server
Very powerful, expensive computer that supports thousands of computers.
Supercomputer
-The faster, most powerful, most expensive computer. Used for application requiring complex mathematical calculations.
Elements of an information system ?
What are the information system elements ?
Data
Hardware
Software
Procedures
People
Computer applications in society ?
Education
Finance
Government
Healthcare
Science
Publishing
Travel
Industry
Question ?
1) Give me few example of who needs and uses a power computer?
Question ?
Engineers
Scientists
Architects
Desktop publishers
Graphic artists
Question ?
2) What are the few functions of a PDA ?
Question ?
Calendar
Appointment book
Address book
Calculator
Notepad
..Bliana Chap 02 Internet
Find the file in Google Groups

Bliana Chap 02 Internet - Presentation Transcript
Chapter 2: The Internet and World Wide Web
Prepared by:Bliana Muhammad Halime
Started by Pentagon’s Advanced Research Program Agency(ARPA) by US Department of Defense.
It allowed scientist to share information at different locations and projects to function even if part of network is disabled.
Original ARPANET consist 4 computers in 4 universities that served as a host on the network.
Evolution of Internet
National Science Foundation (NSF) uses it huge network of 5 supercomputers to connect (NSFNET) with ARPANET. Known as Internet.
The World Wide Web Consortium (W3C) sets standards and guidelines in contributing to the growth of the web.
NSFNET is replaced by companies that provide networks to handle internet traffic.
Internet 2- develop and test advanced network that will benefit internet users in short term future.
Cable Internet Service
DSL ( Digital Service Line)
Fiber to the Premises
Fixed wireless
Cellular radio network
Wi-Fi
Satellite internet service
Connecting to the Internet
Differences betw dial up and broadband internet connections.
Dial-up
Broadband
Requires modem that is connected to computers and land line
Connects to internet via phone line
Slower speed technology
Access through cable television network, regular telephone lines and fiber optic cable.
Does not requires modem for every computers( a modem acts as ports and hotspot).
Connects to internet via radio signal and satellite signals.
High speed technology
Access through wireless ports, router etc.
Access Providers
Internet Service Provider
Online Service Provider
Is a regional or national service provider.
Regional- provides access to a specific geographic area.
National- provides access to cities and towns nationwide.
For dial up access- some offers both local and toll free telephone numbers.
Has members only features. E.g. AOL and MSN.
Provides gateway functionality to Internet.
Provides free access to Internet
Uniquely identifies computer that are connected to the internet.
Relies on IP add to identifies and send data to specific locations.
Internet Protocol Address- consist of four different group of numbers, each separated by a period.
E.g 72.14.207.99 or www.google.com
Domain name is text version of IP add.
Purpose of an IP address and domain name.
Web Browser- application software that allows users to access and view Web pages.
Components of web address
-link(hyperlink) built in connection to web
page.
-URL (Uniform Resource Locator) or web
address.
Purpose of a web browser and the components of a web address.
Enter a word or phrase.
The results is called searched query.
Each word is known as keywords.
The search engine displays the number of hits. (in a form of a list)
Subject directory classifies the topics that u searched.
By clicking at it, it will link you to the web page.
How do u use a search engine?
Portal
Blog
Wiki
Online social network
Web application.
What are the types of websites?
..Adeyinka Chap 03 Application Software
Find the file in Google Groups

Adeyinka Chap 03 Application Software - Presentation Transcript
APPLICATION SOFTWARE
APPLICATION SOFTWARE – this is a program designed to make user more productive, and/or assist them with personal task. application software help to create letters, memos, and reports etc.
THE USES OF APPLICATION SOFTWARE
(1) to make business activities more efficient
(2) to assist with graphic and multimedia project
(3) to support home personal and educational tasks
(4)to facilitate communication
Categories of application software
APPLICATION SOFTWARE CAN BE CATIGORISE INTO FOUR GROUPS
(1) BUSINESS APLICATION SOFTWARE --- this is an application software that assist people in becoming more effective and efficient when performing their day to day activities.eg accounting software,personal information, and the document management
(2)GRAPIC AND MULTIMEDIA SOFTWARE – this are sophisticated software that allow them to work with graphic and multimedia .this software include desktop publishing printing image ,editing photo editing video etc
(3)HOME PERSONAL EDUCATION -- this software provide valuable and through information for all individual popular reference soft ware including encyclopedias dictionaries health media guide
(4) COMMUNICATION SOFTWARE this is a software that transmit information from the encoder which is the sender to the decoder which is the reliever
CHAPTER THREE PRESENTATION BY OMOSUWA .ADEYINKA .O
TYPES OF APPLICATION SOFTWARE
Date base software - this is a structural collection of data it help the user to store retrieve from data base
Word processing software –it enable user to credit and edit document e.g. ms word word pad note pad
Spread sheet software - this software allows users to perform calculation
Presentation software –this is used to display information in form of slide show
MULTIMEDIA SOFTWARE – this allows users to create and play audio video e.g. real and media player
THE ROLE OF SYSTEM SOFT WARE
system software serve as an interface between the user application software and the computer hardware, the user does not communicate directly to the hardware e.g. when the user instruct the application soft ware to print a document, the application send the print instruction to the system software which in turn send the print instruction to the hard ware.
WORKING WITH APPLICATION SOFTWARE
To work or use the application software ,you must instruct the operating system to start the program e.g. you click the all program command and on the start menu then all programs listed is displayed on the start menu. then click the program name on the menu the action instruct the operating system to start the programs, instruction load from a storage menu e.g. when you click print the accessories lead window loads the print program instruction from the computer hard ware disc into the memory.
QUESTION What are the types of application software ?
..Pramilah Chap 04 System Unit
Find the file in Google Groups

Pramilah Chap 04 System Unit - Presentation Transcript
Chapter 4: The Components of the System Unit
By Pramiladevi
What is the system unit?
Case that contain the motherboard, the flat board within the personal computer housing that holds the chips and circuitry that organize the computers activities.
Sometimes called chassis, is made of metal or plastic and protects the internal electronic components from damage.
The electronic components and circuitry of the system unit, such as the processor and memory, usually are part of or are connected to a circuit board called the motherboard.
What is the motherboard?
Sometimes called a system board, is the main circuit board of the system unit.
The motherboard contains several bus lines, or buses, sets of parallel electrical paths that transport electrical signals. The system bus transfers data between CPU and memory. Bus width and speed affect system performance.
Some expansion buses connect to expansion slots on the motherboard and can receive expansion boards (also called interface cards or adapter cards) that enable you to connect various peripheral devices to the computer.
A serial port enables data to be transmitted one bit at a time, while a parallel port transmit a group of bits at a time.
What is the Central Processing Unit (CPU)?
A CPU, or processor, on a chip is a microprocessor.
A microprocessor maybe called a logic chip when it is used to control specialized devices.
A microprocessor contains tiny transistors, electronic switches that may or may not allow current to pass through, representing a 1 or 0 bit, respectively.
The more functions that are combined on a microprocessor, the faster the computer runs, the cheaper it is to make, and the more reliable it is.
The 2 parts of the CPU are the control unit and the arithmetic logic unit, both working together as a team to process the computer’s command.
What is the machine cycle?
Four operation of CPU comprise a machine cycle
Step 1. FETCH
obtain program
instruction
or data item from memory
memory
Step 4. STORE
Write result to
memory
Processor
Step 2.DECODE
Translate instruction
Into commands
Control unit
ALU
Step 3.EXECUTE
Carry out command
What is memory?
Electronic components that store instruction, data, and result.
Consist of one or more chips on motherboard or other circuit board.
Each byte stored in unique location called an address, similar to seats in a concert hall.
What is Random Access Memory(RAM)?
Keeps the instruction and data for whatever programs you are using at the moment.
Divided into two types: static RAM(SRAM),which is faster, and dynamic RAM(DRAM), which is slower and much less expensive, SDRAM and RDRAM are faster and more expensive types of DRAM.
..Uthaya Chap 05 Input
Find the file in Google Groups

Uthaya Chap 05 Input - Presentation Transcript
What Is Input?
Input is any data or instruction entered into the memory of a computer.
By:UthAyA
Difference Among a Program, a Command, and a User Response
*Program is a series of related instructions that tells a computer what tasks to perform and how to perform them.
*Command is an instructions that causes a program to perform a specific action.
*User Response replying to a question displayed by a program to perform certain actions.
->Keyboard is an input that contains keys users press to enter data and instructions into a computer.->Most keyboard also have function keys programmed to issues commands ; toggle keys that switch between two states when press; and keys used to move the insertion point, or cursor , on the screen.
-> Input Device is any hardware component that allows users to enter data and instructions(program, command, and user response)
Mouse is a pointing device that fits under the palm of your hand.
Optical mouse -> emit and sense light to detect the mouse’s movement.
Laser mouse -> uses a laser and is more expensive than an optical mouse.
Air mouse -> allows you to control objects, media players, and slide shows by moving
the mouse in predetermined directions through the air.
Wireless/Cordless mouse -> transmit data using wireless technology.
Touch screen is a touch-sensitive display device.Touch screen that recognize multiple points of contact at the same time are known as multi-touch.
*(Kiosk is a freestanding computer that usually includes a touch screen)
*(Microsoft Surface is a 30-inch tabletop display that allows one or more people to
interact with screen)
Touch-sensitive pad is an input device thatenable users to scroll through.
Various Types Of Pen Input and Other Types of Input for Smart Phone.
*Pen input is stylus or digital pen that u touch on a flat surface, such as a screen on a
monitor, mobile device and a signature capture pad.
*Stylus is a small metal or plastic device that looks like a tiny ink pen but uses
pressure instead of ink.
*Digital pen is features electronic erasers and programmable buttons.
*Handwriting recognition software is a program that translate handwritten letters
and symbols into characters a computer or mobile device can process.
*Signature capture pad captures signatures written with a stylus or pen attached to a device.
*Gamepad controls the movement and actions and object.
*Joystick is a handheld vertical lever that you move to control a simulated vehicle player.
*Wheel is a steering-wheel-type device that you turn to stimulate driving a vehicle.
*Light gun is used to shoot targets as you pull the trigger on the weapon.
*Dance pad is an electronic device, divided into panels, that users press with their feet.
*Motion sensing game controllers such as Wii Remote guide on screen elements by moving a handheld input device in predetermined direction through the air.
How Does Resolution Affect the Quality of a Picture Captured on a Digital Camera?
*Resolution is the number of horizontal and vertical pixels in a display device.
*higher the resolution the better the picture quality.
How Are Voice Recognition, Web Cams, and Video Conferencing Used?
*Voice recognition also called speech recognition is the
computer ‘s capability of distinguishing spoken words.
*Web cam enable users to capture video and still image
and then send or broadcast over the internet.
*Video conference enable two or more users to transmit audio and video data.
Scanner or optic scanner is a light sensing input device that reads printed text and graphic and translate the results into a form the computer can process.
Examples:
*Flatbed scanner
*Optical reader
*Optical character recognition(OCR)
*Optical mark recognition(OMR)
*bar code reader/bar code scanner
*Radio frequency identification(RFID)
*magnetic stripe card reader
*magnetic ink character recognition(MICR)
What Are Various Biometric Devices?
*Biometric device translate a personal characteristic into digital
code that is compared with a digital code stored in the
computer to identify an individual.
Devices:
*fingerprint reader
*face recognition system
*hand geometry system
*voice verification system
*signature verification system
*retinal scanner
..Mahendran Chap 06 Output
Find the file in Google Groups

Mahendran Chap 06 Output - Presentation Transcript
OUTPUT
processed into useful form
4 Types of Output:
Text
Graphics
Audio
Video
Devices – Hardware component that conveys
information to one or more people
Display Devices
Output display that visually conveys text, graphics, and video information
2 Types of Display Devices
Flat-panel Displays
( LCD Monitors[uses a liquid crystal display to produce images])
( LCD Screens[produce colour using either active –matrix or passive matrix technology])
( Plasma Monitors[display device that uses gas plasma technology ,which sandwiches a layer of gas between two glass plates)
* LCD Technology-uses a liquids compound to present information on a device.
*LCD Quality-depends primarily on its resolution ,response time,brightness,dot pitch ,and contrast ratio.
CRT Monitors
Speaker, Headphones and Ear buds
Audio output device is a component of a computer that produces music, speech, and sounds.
Printer
Output device that produces text and graphics on a physical medium such as paper
3 Type of Printer
Nonimpact Printers
(forms characters and graphics on a piece of paper without actually striking the paper)
Ink-Jet Printers
(forms characters and graphics by spraying tiny drops of liquid ink onto a piece of paper )
Photo Printers
(a colour printer that produces photo-lab-quality pictures)
Printer ( cont )
Laser Printers
(a high speed ,high –quality nonimpact printer that operates in a manner similar to a copy machine,creating images using a laser beam and powdered ink,called toner
Thermal Printer
(generates images by pushing electrically heated pins against heat-sensitive paper)
Mobile Printer
(allows a mobile user to print from a notebook computer or other mobile device)
Printer ( cont )
Label and Postage Printers
(prints on an adhesive –type material that can be placed on a variety of items )
Plotters and Large-Format Printers
(sophisticated printers used to produce high-quality drawing )
Impact Printers
(forms characters and graphics on a piece of paper by striking a mechanism against an linked ribbon that physically contacts the paper)
Other Output Devices
Data Projectors text and images displaying on a
(device that takes the computer screen and projects them onto a larger screen so that an audience can see the image clearly)
Interactive Whiteboards
(a touch –sensitive device)
Force-Feedback Game Controllers and Tactile Output
..Faizan Chap 07 Storage
Find the file in Google Groups

Faizan Chap 07 Storage - Presentation Transcript
STORAGE CHAPTER 7 by Faizan Tariq
kilobyte (KB) 1 thousand Megabyte (MB) 1 million Gigabyte (GB) 1 billion Terabyte (TB) 1 trillion Petabyte (PB) 1 quadrillion STORAGE
What is Storage?
holds data, instructions, and information for future use
storage medium is physical material used for storage
What is Capacity?
number of bytes (characters) a storage medium can hold
What is a storage device?
Hardware that records and retrieves items from storage media
Reading : Process of transferring items from storage media to memory
Functions as source of input
Writing : Process of transferring items from memory to storage media
creates output
STORAGE
STORAGE
What are tracks and sectors?
Tracks is narrow recording band that forms full circle disk
Sectors stores up to 512 bytes of data
What is a floppy disk ?
Portable , inexpensive storage medium (also called as diskette)
Magnetic disks
What is a floppy disk drive ?
Device that reads from and writes to floppy disk
Also called secondary storage
Floppy disk drive built into a desktop computer
External floppy disk drive attaches a computer with a cable
Magnetic disks
How do you compute a disk's storage capacity?
Multiply number of sides, number of tracks, number of sectors per track, and number of bytes per sector
For high density disk 2 sides x 80 tracks x 18 sectors per track x 512 bytes per sector = 1,474,560 bytes
Characteristics of a 3.5 inch High density Floppy disk
Capacity: 1.44 MB Slides: 2 Tracks: 80 Sector per track: 18 Bytes per second: 512 Sector per disk: 2880
Magnetic disks
What is a Zip disk ?
Magnetic medium that stores 100 MB to 750 MB of data
Used to back up and to transfer files
: backup is duplicate of files, program, or disk in
case of original is lost.
Zip disk requires a Zip drive high capacity drive that reads
and writes on a Zip disk
What is a hard disk ?
High capacity storage
Consist of several inflexible, circular platters that stores items electronically
Components enclosed in alright, sealed case for protection
Advertised capacity 120GB Platters 3 Read/write heads 6 Cylinders 16,383 Bytes per seconds 512 Sectors per track 63 Sectors per drive 234,441,648 Revolution per minute 7,200 Transfer rate 133MB per second Access time 8.9 ms Magnetic disks
What are characteristics of a hard disk?
Simple hard drive characteristics
What is a cylinder ?
Vertical section of track through all platters , single movement of read/write head
arms access all platters in cylinder
Magnetic disks
How does a hard disk work ?
Step 1 : circuit board controls movement of head actuator and a small motor.
Step 2 : small motor spins platter while computer is running.
Step 3 : when software request a disk access, read/write heads determine current or new location of data.
Step 4 : head actuator positions read/write arms over correct location on platters to read or write data.
What is a head crash ?
Occurs when read/write head touches platter surface
Spinning creates cushion of air that floats read/write above platter
Clearance between head and platter is approximately two- millionths of an inch
A smoke particle, dust particle, or human hair could render drive unusable
Magnetic disks
What is a miniature hard disk ?
Provide users with greater storage capacities than flash memory
Some have a form factor of less than 1 inch
Storage capacities range from 2 GB to 100 GB
What is online storage ?
Service on web that provides storage for minimum monthly fee
Files can be accessed from any computer with web access
Large file can be downloaded instantly
Others can be authorized to access your data
Magnetic disks
What are external hard disk and removable hard disk ?
Used to back up or transfer files
External hard disk : freestanding hard disk that connects to system unit
Removable hard disk : hard disk that you insert and remove from hard drive
What are optical discs ?
Flat, round, portable metal discs made of metal, plastic, and lacquer
Can be read only or read/write
Most PCs include an optical disc drive
What is a CD-ROM ?
Compact disc read- only memory
Cannot erase or modify contents
Typically holds 650 MB to 1 GB
Commonly used to distribute multimedia and complex software
Optical disks
What is a DVD-ROM (digital versatile disc-ROM or digital video disc-ROM)?
Highly capacity disc capable of storing 4.7 GB to 17 GB
Must have DVD –ROM drive or DVD player to read DVD -ROM
Stores databases, music, complex software, and movies
How does a laser read data on an optical disc ?
Step 1 . laser diode shines a light beam toward disc
Step 2 . if light strikes a it scatters, if a light strikes a land, it strike a land , it is reflected back towards diode.
Step 3 . reflected light is deflected to a light-sensing diode, which send digital signals of 1 to computer. Absence of reflected light is read as digital signal of 0.
Optical disks
How should you take care of an optical disc ?
Do not expose the disc to excessive heat or sunlight
Do not smoke ,eat or drink near a disc
Do not stack disc
Do not touch the underside of the disc
Do store the disc in a jewel box when not in use
Do hold the disc by its edges
What are CD-Rs and CD- RWs?
CD-R (compact disc – recordable) disc you can write once
Must have CD recorder or CD-R drive
Cannot erase discs contents
CD-RW (compact disc- rewriteable) erasable disc you can write on multiple times
Must have CD-RW software and CD-RW drive
Tape
What is tape?
Magnetically coated plastic ribbon capable of storing large amounts of data at low cost
Primarily used for backup
How is data stored on a tape ?
Sequential access
Reads and write data consecutively like a music tape
Unlike direct access – used on floppy, zip disks , hard disks, CDs and DVDs – which can locate particular item immediately
..Amr Chap 08 Operating Systems & Utility Programs
Find the file in Google Groups

Amr Chap 08 Operating Systems & Utility Programs - Presentation Transcript
Operating Systems & Utility ProgramsChapter 8
By Amr Aborig.
What is System Software?
System software consists of the programs that control or maintain the operations of the computer and its devices.
Two types of system software .
Operating systems
Utility programs.
An operating system (OS)is a set of programs containing instructions that work together to coordinate all the activities among computer hardware resources .
Operating systems
Operating systems are divided in to three basic categories :
1.Stand-alone OS: is a complete operating system that works on a desktop computer ,notebook computer, or mobile computing device.
Names of Stand-alone operating systems: DOS /Early Windows Versions (Windows 3.x,Windows 95, Windows NT Workstation, Windows 98, Windows 2000 professional, Windows Millennium Edition, Windows XP)/Windows Vista/ Mac OS X/UNIX/Linux.
2.Server OS: is an operating system that is designed specifically to support a network.
Names of Server operating systems: Early Windows server versions(Windows NT Server, Windows 2000 server, Windows Server 2003)//Windows Server 2008 /UNIX /Linux /Solaris/ Netware.
-Embedded OS :The operating system on mobile devices and many consumer electronics.
-Names of embedded OS :Windows Embedded CE/Windows Mobile/ Palm OS / i Phones OS /BlackBerry/ Embedded Linux /Symbian OS.
~The Boot Process~
-Is the process of starting or restarting a computer is called booting.
-When turning on a computer that has been powered off completely, you are performing a cold boot. A warm boot is the process of using the operating system to restart a computer.
-Steps of the boot process:-
1-The power supply sends a signal to the components in the system unit.
2-The processor finds the ROM chips(s) that contains the BIOS (basic input/output system.
3-The BIOS performs the POST (power on self test) ,which checks components ,such as the mouse , keyboard &adapter cards.
4-The results of the POST are compared with data in a CMOS (Complementary metal-oxide semiconductor) chip.
5-The BIOS may look for the system files on a USB flash drive or on an optical disc drive or may look directly on drive C (hard disk).
6-The system files and the kernel of the operating system load into memory (RAM) from storage (i.e., hard disk).
7-The operating system loads configuration information , may request user information , starts several background processes , and displays the desktop on the screen
Functions of operating systems
-Starting and shutting down a computer (cold or warm boot).
-Providing a user interface.
-Managing computers & Memory.
-coordinating Tasks.
-Configuring Devices.
-Establishing an Internet connection.
-Monitoring Performance.
-Providing file management & other utilities.
-And automatically updating itself &certain utility programs.
-Control a network & administer security.
What is a utility program?
A utility program , also called a utility, is a type of software that allows a user to perform maintenance- type tasks ,usually related to managing a computer , its devices or its programs.
Functions of utility programs
Managing/searching for files.
Viewing images
Uninstalling programs
Cleaning up/Defragmenting disks
Backing up files & disks
Setting up screen savers
Securing a computer from unauthorized eccess
Protecting against viruses/removing spyware & adware
Filtering Internet content
Compressing files
Playing media Files/Burning optical discs.
& Maintaining a personal computer.
Q?
1-What is system software? Name the types of system software.
2-What does POST ,BIOS & CMOS stand for and name their functions?
..Dennis Chap 09 Data Communication
Find the file in Google Groups

Dennis Chap 09 Data Communication - Presentation Transcript
By:
Amanta Dennis Saputra
(Diploma in Marketing)
Process in which two or more devices transfer data, instruction, and information.
Wireless Messaging Services
Wireless Internet Access Point
Cybercafés
Global Positioning System
Groupware
Voicemail
Collaboration
Web Service
Is a collections of computers and devices connected together via communications devices and transmission media.
Facilitating communications
Sharing Hardware
Sharing Data and Information
Sharing Software
Transferring Funds
LAN ( is a network that connects computers and devices in a limited geographical area, such as home, office building, etc)
WLAN ( is a LAN that uses no physical wires)
MAN (is a High-speed network that connects local area network in a metropolitan area, such as city or town)
WAN (is a network covers a large geographical area, such as a city, a country, or the world)
Dial-Up Lines (temporary connection that uses one or more analog telephone lines for communications)
Dedicated Lines (type of always-on connections that is established between two communications devices)
ISDN Lines (faster than Dial-Up)
DSL (fast speeds on existing standard copper telephone wiring)
FTTP ( uses fiber-optic to provide extremely high-speed Internet access to users physical permanent locations)
ATM (a service that carries voice, data, video, and multimedia at very high speeds)
Dial-up Modems (communications device that can convert digital signals to analog and analog signals to digital signals)
Digital Modems (communications device that sends and receives data and information to and from a digital line)
Wireless Modems
Network Cars (communications device that enables a computer or device that doesn’t have built-in networking capability to access a network)
Wireless access point (central communications device that allows computer and devices to transfer data wirelessly)
Routers (communications devices that connects multiple computers or other routers together and transmits data to its correct destination on a network)
Connect to the Internet at the same time
Share a single high-speed Internet connection
Access files and programs on the other computers in the house
Share peripherals such as a printer, scanner, external hard disk
Play multiplayer game with players on others computer in the house
Connect game consoles to the Internet
Ethernet (network standard that specifies no central computer or device on the network should control when data can be transmitted)
Power line Cable Network (network that uses the same lines that bring electricity into the house)
Phone line Network (an easy-to-install and inexpensive network that uses existing telephone lines in the home)
1. What is communication in computer ??
2. What is communication device ??
..Gevita Chap 10 Database Management
Find the file in Google Groups

Gevita Chap 10 Database Management - Presentation Transcript
CHAPTER 10 DATABASE MANAGEMENT PRESENTED BY GEVITA
DATABASE,DATA& INFORMATION
7 type data
- Data integrity
- Quality Of valuable information
- Hierarchy of data
- Characters
- Fields
- Records
- Files
MAINTAINING DATA
Adding Records
Modifying Records
Deleting Records
Validating Data
FILE PROCESSING VERSUS DATABASES File processing system Data Redundancy Isolated data The database Approach Disadvantages of database Many programs and users share the data in the database.
Can be more complex than a file processing system.
Store a lot in single file.
DATABASE MANAGEMENT SYSTEM
4 TYPE OF DATABASE
1. File Retrieval & Maintenance
2. Query Language
3. Data Security
4. Backup & Recovery
Relational, Object Oriented & Multidimensional databases
1. Relational
- Stores data in tables
2. Object- Oriented Database
- store data in object
3. Multidimensional
- store data dimensions
Web Database & Types
CHAPTER REVIEW -Database, Data and information -Maintaining Data -File Processing versus Databases -Database Management System -Relational, Object Oriented & Multidimensional - Web Database
What is the examples of application for an object-oriented database?
2. What is the 2 major weaknesses of file processing system?
1. A multimedia database, a groupware database, a computer –aided design, a hypertext database. 2. Data redundancy and isolated data THANK YOU!
..Chen-special-topic-01-Multimedia
Find the file in Google Groups

Chen-special-topic-01-Multimedia - Presentation Transcript
Multimedia
Multimedia is media and content that uses a combination of different content forms. The term can be used as a noun (a medium with multiple content forms) or as an adjective describing a medium as having multiple content forms. The term is used in contrast to media which only use traditional forms of printed or hand-produced material. Multimedia includes a combination of text, audio, still images, animation, video, and interactivity content forms.
Multimedia is usually recorded and played, displayed or accessed by information content processing devices, such as computerized and electronic devices, but can also be part of a live performance. Multimedia (as an adjective) also describes electronic media devices used to store and experience multimedia content. Multimedia is distinguished from mixed media in fine art; by including audio, for example, it has a broader scope. The term "rich media" is synonymous for interactive multimedia. Hypermedia can be considered one particular multimedia application.
What are some popular graphics and multimedia software products?
Graphics and Multimedia Software
Next
p. 151 Fig. 3-19
Graphics and Multimedia Software
Next
What is computer-aided design (CAD)?
Sophisticated application software that allows you to create engineering, architectural, and scientific designs
p. 151 Fig. 3-20
Graphics and Multimedia Software
Next
What is desktop publishing software?
Enables you to design and produce sophisticated documents that contain text, graphics, and many colors
p. 152 Fig. 3-21
Graphics and Multimedia Software
Next
What is paint/image editing software?
Used to create and modify graphical images
Sometimes called illustration software
p. 152 Fig. 3-22
Graphics and Multimedia Software
Next
What is professional photo editing software?
Allows users to customize digital photographs
Save images in a variety of file formats
p. 152 - 153 Fig. 3-23
Graphics and Multimedia Software
Next
What is video and audio editing software?
Video editing software allows you to modify a segment of a video, called a clip
Audio editing software allows you to modify audio clips
p. 153 Fig. 3-24
Graphics and Multimedia Software
Next
What is multimedia authoring software?
Allows you to combine text, graphics, audio, video, and animation in an interactive application
p. 154 Fig. 3-25
Graphics and Multimedia Software
organize
manage
maintain
Next
What is Web page authoring software?
Helps users of all skill levels to create Web pages
Some application software programs include Web page authoring programs
graphicalimages
video
Web pagesand/orWeb sites
animation
audio
p. 154
Media player is a term typically used to describe computer software for playing back multimedia files. Most software media players support an array of media formats, including both audio and video files.
Media Player
Types of media player.
Windows Media Player
iTunes
Winamp
Qq Player
Qvod player
Media Player
Media Player
Every media player uses the same function as shown in my swf file – play and stop button function. A movie that is played in a media player is said to be having the synchronization of audio and video in a fixed frame setting.
Media Player(ext)
..Wong Pau Tung-special-topic-02-Virus
Find the file in Google Groups

Wong Pau Tung-special-topi-02-Virus - Presentation Transcript
Internet and Network Attacks
What are viruses , worms , and Trojan horses ?
p. 558 Virus is a potentially damaging computer program
Worm copies itself repeatedly, using up resources and possibly shutting down computer or network
Trojan horse hides within or looks like legitimate program until triggered Payload (destructive event) that is delivered when you open file, run infected program, or boot computer with infected disk in disk drive Can spread and damage files Does not replicate itself on other computers Next
Internet and Network Attacks
How can a virus spread through an e-mail message?
p. 559 Fig. 11-2 Step 1. Unscrupulous programmers create a virus program. They hide the virus in a Word document and attach the Word document to an e-mail message. Step 2. They use the Internet to send the e-mail message to thousands of users around the world. Step 3b. Other users do not recognize the name of the sender of the e-mail message. These users do not open the e-mail message. Instead they delete the e-mail message. These users’ computers are not infected with the virus. Step 3a. Some users open the attachment and their computers become infected with the virus. Next
Internet and Network Attacks Video: Attack of the Mobile Viruses Next CLICK TO START
Internet and Network Attacks
How can you protect your system from a macro virus?
p. 560 Fig. 11-3
Set macro security level in applications that allow you to write macros
Set security level so that warning displays that document contains macro
Macros are instructions saved in an application, such as word processing or spreadsheet program
Next
Internet and Network Attacks
What is an antivirus program ?
p. 560 - 561 Fig. 11-4
Identifies and removes computer viruses
Most also protect against worms and Trojan horses
Next
Internet and Network Attacks
What is a virus signature ?
p. 561 Fig. 11-5
Specific pattern of virus code
Also called virus definition
Antivirus programs look for virus signatures
Next
Internet and Network Attacks
How does an antivirus program inoculate a program file?
p. 561 Keeps file in separate area of hard disk Next Records information about program such as file size and creation date Attempts to remove any detected virus Uses information to detect if virus tampers with file Quarantines infected files that it cannot remove
Internet and Network Attacks
What are some tips for preventing virus, worm, and Trojan horse infections?
p. 562 Install a personal firewall program If the antivirus program flags an e-mail attachment as infected, delete the attachment immediately Never start a computer with removable media inserted Never open an e-mail attachment unless you are expecting it and it is from a trusted source Install an antivirus program on all of your computers Check all downloaded programs for viruses, worms, or Trojan horses Next Click to view Web Link, click Chapter 11, Click Web Link from left navigation, then click Virus Hoaxes below Chapter 11
Tuesday, December 15, 2009
DESIGNING TIC TAC TOE PROGRAM USING C++ LANGUAGE
Find the file in Google Groups

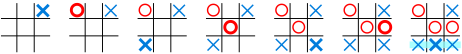
Tic-tac-toe, also spelled tick tack toe, and alternatively called noughts and crosses, X's and O's, and many other names, is a pencil-and-paper game for two players, O and X, who take turns marking the spaces in a 3×3 grid, usually X going first. The player who succeeds in placing three respective marks in a horizontal, vertical or diagonal row wins the game.
The following example game is won by the first player, X:
Players soon discover that best play from both parties leads to a draw. Hence, tic-tac-toe is most often played by young children; when they have discovered an unbeatable strategy they move on to more sophisticated games such as chess or chinese checkers. This reputation for ease has led to casinos offering gamblers the chance to play tic-tac-toe against trained chickens—though the chicken is advised by a computer program.
How do we design a simple DOS program for two players?
First of all, we need to approach the game structure systematically using problem decomposition, i.e., breaking down the main problem into small manageable chunks of problem.
EXAMPLE 1
basic procedures:
1. main() - to control the program
2. PlayGame() - to control the game session
3. GameRound() - to control each player's turn
4. DisplayPanel() - to control the game display
5. DisplaySymbol() - to control the symbol display
6. CheckWin() - to determine winning condition
7. InitVar() - to initialize variables before a game session starts
optional procedures:
8. GetPlayerNames() - to get the name of each players
9. PlaySound() - to play certain sounds to accompany events in the game
10. ComputerPlayer() - to play against the human
Monday, December 14, 2009
Sunday, November 1, 2009
Ais Romney 2006 Slides 06 Control And Ais
Find the file in Google Groups

Ais Romney 2006 Slides 06 Control And Ais - Presentation Transcript
HAPTER 6 Control and Accounting Information Systems
INTRODUCTION
Questions to be addressed in this chapter:
What are the basic internal control concepts, and why are computer control and security important?
What is the difference between the COBIT, COSO, and ERM control frameworks?
What are the major elements in the internal environment of a company?
What are the four types of control objectives that companies need to set?
What events affect uncertainty, and how can they be identified?
How is the Enterprise Risk Management model used to assess and respond to risk?
What control activities are commonly used in companies?
How do organizations communicate information and monitor control processes?
INTRODUCTION
Why AIS Threats Are Increasing
Control risks have increased in the last few years because:
There are computers and servers everywhere, and information is available to an unprecedented number of workers.
Distributed computer networks make data available to many users, and these networks are harder to control than centralized mainframe systems.
Wide area networks are giving customers and suppliers access to each other’s systems and data, making confidentiality a major concern.
INTRODUCTION
Historically, many organizations have not adequately protected their data due to one or more of the following reasons:
Computer control problems are often underestimated and downplayed.
Control implications of moving from centralized, host-based computer systems to those of a networked system or Internet-based system are not always fully understood.
Companies have not realized that data is a strategic resource and that data security must be a strategic requirement.
Productivity and cost pressures may motivate management to forego time-consuming control measures.
INTRODUCTION
Some vocabulary terms for this chapter:
A threat is any potential adverse occurrence or unwanted event that could injure the AIS or the organization.
The exposure or impact of the threat is the potential dollar loss that would occur if the threat becomes a reality.
The likelihood is the probability that the threat will occur.
INTRODUCTION
Control and Security are Important
Companies are now recognizing the problems and taking positive steps to achieve better control, including:
Devoting full-time staff to security and control concerns.
Educating employees about control measures.
Establishing and enforcing formal information security policies.
Making controls a part of the applications development process.
Moving sensitive data to more secure environments.
INTRODUCTION
To use IT in achieving control objectives, accountants must:
Understand how to protect systems from threats.
Have a good understanding of IT and its capabilities and risks.
Achieving adequate security and control over the information resources of an organization should be a top management priority.
INTRODUCTION
Control objectives are the same regardless of the data processing method, but a computer-based AIS requires different internal control policies and procedures because:
Computer processing may reduce clerical errors but increase risks of unauthorized access or modification of data files.
Segregation of duties must be achieved differently in an AIS.
Computers provide opportunities for enhancement of some internal controls.
INTRODUCTION
One of the primary objectives of an AIS is to control a business organization.
Accountants must help by designing effective control systems and auditing or reviewing control systems already in place to ensure their effectiveness.
Management expects accountants to be control consultants by:
Taking a proactive approach to eliminating system threats; and
Detecting, correcting, and recovering from threats when they do occur.
INTRODUCTION
It is much easier to build controls into a system during the initial stage than to add them after the fact.
Consequently, accountants and control experts should be members of the teams that develop or modify information systems.
OVERVIEW OF CONTROL CONCEPTS
In today’s dynamic business environment, companies must react quickly to changing conditions and markets, including steps to:
Hire creative and innovative employees.
Give these employees power and flexibility to:
Satisfy changing customer demands;
Pursue new opportunities to add value to the organization; and
Implement process improvements.
At the same time, the company needs control systems so they are not exposed to excessive risks or behaviors that could harm their reputation for honesty and integrity.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
This objective includes prevention or timely detection of unauthorized acquisition, use, or disposal of material company assets.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
Accurate and reliable information is provided.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
Accurate and reliable information is provided.
There is reasonable assurance that financial reports are prepared in accordance with GAAP.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
Accurate and reliable information is provided.
There is reasonable assurance that financial reports are prepared in accordance with GAAP.
Operational efficiency is promoted and improved.
This objective includes ensuring that company receipts and expenditures are made in accordance with management and directors’ authorizations.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
Accurate and reliable information is provided.
There is reasonable assurance that financial reports are prepared in accordance with GAAP.
Operational efficiency is promoted and improved.
Adherence to prescribed managerial policies is encouraged.
OVERVIEW OF CONTROL CONCEPTS
Internal control is the process implemented by the board of directors, management, and those under their direction to provide reasonable assurance that the following control objectives are achieved:
Assets (including data) are safeguarded.
Records are maintained in sufficient detail to accurately and fairly reflect company assets.
Accurate and reliable information is provided.
There is reasonable assurance that financial reports are prepared in accordance with GAAP.
Operational efficiency is promoted and improved.
Adherence to prescribed managerial policies is encouraged.
The organization complies with applicable laws and regulations .
OVERVIEW OF CONTROL CONCEPTS
Internal control is a process because:
It permeates an organization’s operating activities.
It is an integral part of basic management activities.
Internal control provides reasonable , rather than absolute, assurance, because complete assurance is difficult or impossible to achieve and prohibitively expensive.
OVERVIEW OF CONTROL CONCEPTS
Internal control systems have inherent limitations, including:
They are susceptible to errors and poor decisions.
They can be overridden by management or by collusion of two or more employees.
Internal control objectives are often at odds with each other.
EXAMPLE: Controls to safeguard assets may also reduce operational efficiency.
OVERVIEW OF CONTROL CONCEPTS
Internal controls perform three important functions:
Preventive controls
Deter problems before they arise.
OVERVIEW OF CONTROL CONCEPTS
Internal controls perform three important functions:
Preventive controls
Detective controls
Discover problems quickly when they do arise.
OVERVIEW OF CONTROL CONCEPTS
Internal controls perform three important functions:
Preventive controls
Detective controls
Corrective controls
Remedy problems that have occurred by:
Identifying the cause;
Correcting the resulting errors; and
Modifying the system to prevent future problems of this sort.
OVERVIEW OF CONTROL CONCEPTS
Internal controls are often classified as:
General controls
Those designed to make sure an organization’s control environment is stable and well managed.
They apply to all sizes and types of systems.
Examples: Security management controls.
OVERVIEW OF CONTROL CONCEPTS
Internal controls are often classified as:
General controls
Application controls
Prevent, detect, and correct transaction errors and fraud.
Are concerned with accuracy, completeness, validity, and authorization of the data captured, entered into the system, processed, stored, transmitted to other systems, and reported.
OVERVIEW OF CONTROL CONCEPTS
An effective system of internal controls should exist in all organizations to:
Help them achieve their missions and goals
Minimize surprises
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
In 1977, Congress passed the Foreign Corrupt Practices Act , and to the surprise of the profession, this act incorporated language from an AICPA pronouncement.
The primary purpose of the act was to prevent the bribery of foreign officials to obtain business.
A significant effect was to require that corporations maintain good systems of internal accounting control.
Generated significant interest among management, accountants, and auditors in designing and evaluating internal control systems.
The resulting internal control improvements weren’t sufficient.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
In the late 1990s and early 2000s, a series of multi-million-dollar accounting frauds made headlines.
The impact on financial markets was substantial, and Congress responded with passage of the Sarbanes-Oxley Act of 2002 (aka, SOX ).
Applies to publicly held companies and their auditors
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
The intent of SOX is to:
Prevent financial statement fraud
Make financial reports more transparent
Protect investors
Strengthen internal controls in publicly-held companies
Punish executives who perpetrate fraud
SOX has had a material impact on the way boards of directors, management, and accountants operate.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
Has five members, three of whom cannot be CPAs.
Charges fees to firms to fund the PCAOB.
Sets and enforces auditing, quality control, ethics, independence, and other standards relating to audit reports.
Currently recognizes FASB statements as being generally accepted.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
They must report specific information to the company’s audit committee, such as:
Critical accounting policies and practices
Alternative GAAP treatments
Auditor-management disagreements
Audit partners must be rotated periodically.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
Auditors cannot perform certain non-audit services, such as:
Bookkeeping
Information systems design and implementation
Internal audit outsourcing services
Management functions
Human resource services
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
Permissible non-audit services must be approved by the board of directors and disclosed to investors.
Cannot audit a company if a member of top management was employed by the auditor and worked on the company’s audit in the past 12 months.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
New rules for audit committees
Members must be on the company’s board of directors and must otherwise be independent of the company.
One member must be a financial expert.
The committee hires, compensates, and oversees the auditors, and the auditors report directly to the committee.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
New rules for audit committees
New rules for management
The CEO and CFO must certify that:
The financial statements and disclosures are fairly presented, were reviewed by management, and are not misleading.
Management is responsible for internal controls.
The auditors were advised of any material internal control weaknesses or fraud.
Any significant changes to controls after management’s evaluation were disclosed and corrected.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
New rules for audit committees
New rules for management
If management willfully and knowingly violates the certification, they can be:
Imprisoned up to 20 years.
Fined up to $5 million.
Management and directors cannot receive loans that would not be available to people outside the company.
They must disclose on a rapid and current basis material changes to their financial condition.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
New rules for audit committees
New rules for management
New internal control requirements
New internal control requirements:
Section 404 of SOX requires companies to issue a report accompanying the financial statements that:
States management is responsible for establishing and maintaining an adequate internal control structure and procedures.
Contains management’s assessment of the company’s internal controls.
Attests to the accuracy of the internal controls, including disclosures of significant defects or material noncompliance found during the tests.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Important aspects of SOX include:
Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession.
New rules for auditors
New rules for audit committees
New rules for management
New internal control requirements
SOX also requires that the auditor attests to and reports on management’s internal control assessment.
Each audit report must describe the scope of the auditor’s internal control tests.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
After the passage of SOX, the SEC further mandated that:
Management must base its evaluation on a recognized control framework, developed using a due-process procedure that allows for public comment. The most likely framework is the COSO model discussed later in the chapter.
The report must contain a statement identifying the framework used.
Management must disclose any and all material internal control weaknesses.
Management cannot conclude that the company has effective internal control if there are any material weaknesses.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Levers of Control
Many people feel there is a basic conflict between creativity and controls.
Robert Simons has espoused four levers of controls to help companies reconcile this conflict:
A concise belief system
Communicates company core values to employees and inspires them to live by them.
Draws attention to how the organization creates value.
Helps employees understand management’s intended direction.
Must be broad enough to appeal to all levels.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Levers of Control
Many people feel there is a basic conflict between creativity and controls.
Robert Simons has espoused four levers of controls to help companies reconcile this conflict:
A concise belief system
A boundary system
Helps employees act ethically by setting limits beyond which they must not pass.
Does not create rules and standard operating procedures that can stifle creativity.
Encourages employees to think and act creatively to solve problems and meet customer needs as long as they operate within limits such as:
Meeting minimum standards of performance
Shunning off-limits activities
Avoiding actions that could damage the company’s reputation.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Levers of Control
Many people feel there is a basic conflict between creativity and controls.
Robert Simons has espoused four levers of controls to help companies reconcile this conflict:
A concise belief system
A boundary system
A diagnostic control system
Ensures efficient and effective achievement of important controls.
This system measures company progress by comparing actual to planned performance.
Helps managers track critical performance outcomes and monitor performance of individuals, departments, and locations.
Provides feedback to enable management to adjust and fine-tune.
SOX AND THE FOREIGN CORRUPT PRACTICES ACT
Levers of Control
Many people feel there is a basic conflict between creativity and controls.
Robert Simons has espoused four levers of controls to help companies reconcile this conflict:
A concise belief system
A boundary system
A diagnostic control system
An interactive control system
Helps top-level managers with high-level activities that demand frequent and regular attention. Examples:
Developing company strategy.
Setting company objectives.
Understanding and assessing threats and risks.
Monitoring changes in competitive conditions and emerging technologies.
Developing responses and action plans to proactively deal with these high-level issues.
Also helps managers focus the attention of subordinates on key strategic issues and to be more involved in their decisions.
Data from this system are best interpreted and discussed in face-to-face meetings.
CONTROL FRAMEWORKS
A number of frameworks have been developed to help companies develop good internal control systems. Three of the most important are:
The COBIT framework
The COSO internal control framework
COSO’s Enterprise Risk Management framework (ERM)
CONTROL FRAMEWORKS
A number of frameworks have been developed to help companies develop good internal control systems. Three of the most important are:
The COBIT framework
The COSO internal control framework
COSO’s Enterprise Risk Management framework (ERM)
CONTROL FRAMEWORKS
COBIT Framework
Also know as the Control Objectives for Information and Related Technology framework.
Developed by the Information Systems Audit and Control Foundation (ISACF).
A framework of generally applicable information systems security and control practices for IT control.
CONTROL FRAMEWORKS
The COBIT framework allows:
Management to benchmark security and control practices of IT environments.
Users of IT services to be assured that adequate security and control exists.
Auditors to substantiate their opinions on internal control and advise on IT security and control matters.
CONTROL FRAMEWORKS
The framework addresses the issue of control from three vantage points or dimensions:
Business objectives
To satisfy business objectives, information must conform to certain criteria referred to as “business requirements for information.”
The criteria are divided into seven distinct yet overlapping categories that map into COSO objectives:
Effectiveness (relevant, pertinent, and timely)
Efficiency
Confidentiality
Integrity
Availability
Compliance with legal requirements
Reliability
CONTROL FRAMEWORKS
The framework addresses the issue of control from three vantage points or dimensions:
Business objectives
IT resources
Includes:
People
Application systems
Technology
Facilities
Data
CONTROL FRAMEWORKS
The framework addresses the issue of control from three vantage points or dimensions:
Business objectives
IT resources
IT processes
Broken into four domains
Planning and organization
Acquisition and implementation
Delivery and support
Monitoring
CONTROL FRAMEWORKS
COBIT consolidates standards from 36 different sources into a single framework.
It is having a big impact on the IS profession.
Helps managers to learn how to balance risk and control investment in an IS environment.
Provides users with greater assurance that security and IT controls provided by internal and third parties are adequate.
Guides auditors as they substantiate their opinions and provide advice to management on internal controls.
CONTROL FRAMEWORKS
A number of frameworks have been developed to help companies develop good internal control systems. Three of the most important are:
The COBIT framework
The COSO internal control framework
COSO’s Enterprise Risk Management framework (ERM)
CONTROL FRAMEWORKS
COSO’s Internal Control Framework
The Committee of Sponsoring Organizations (COSO) is a private sector group consisting of:
The American Accounting Association
The AICPA
The Institute of Internal Auditors
The Institute of Management Accountants
The Financial Executives Institute
CONTROL FRAMEWORKS
In 1992, COSO issued the Internal Control Integrated Framework :
Defines internal controls.
Provides guidance for evaluating and enhancing internal control systems.
Widely accepted as the authority on internal controls.
Incorporated into policies, rules, and regulations used to control business activities.
CONTROL FRAMEWORKS
COSO’s internal control model has five crucial components:
Control environment
The core of any business is its people.
Their integrity, ethical values, and competence make up the foundation on which everything else rests.
CONTROL FRAMEWORKS
COSO’s internal control model has five crucial components:
Control environment
Control activities
Policies and procedures must be established and executed to ensure that actions identified by management as necessary to address risks are, in fact, carried out.
CONTROL FRAMEWORKS
COSO’s internal control model has five crucial components:
Control environment
Control activities
Risk assessment
The organization must be aware of and deal with the risks it faces.
It must set objectives for its diverse activities and establish mechanisms to identify, analyze, and manage the related risks.
CONTROL FRAMEWORKS
COSO’s internal control model has five crucial components:
Control environment
Control activities
Risk assessment
Information and communication
Information and communications systems surround the control activities.
They enable the organization’s people to capture and exchange information needed to conduct, manage, and control its operations.
CONTROL FRAMEWORKS
COSO’s internal control model has five crucial components:
Control environment
Control activities
Risk assessment
Information and communication
Monitoring
The entire process must be monitored and modified as necessary.
CONTROL FRAMEWORKS
A number of frameworks have been developed to help companies develop good internal control systems. Three of the most important are:
The COBIT framework
The COSO internal control framework
COSO’s Enterprise Risk Management framework (ERM)
CONTROL FRAMEWORKS
Nine years after COSO issued the preceding framework, it began investigating how to effectively identify, assess, and manage risk so organizations could improve the risk management process.
Result: Enterprise Risk Manage Integrated Framework (ERM)
An enhanced corporate governance document.
Expands on elements of preceding framework.
Provides a focus on the broader subject of enterprise risk management.
CONTROL FRAMEWORKS
Intent of ERM is to achieve all goals of the internal control framework and help the organization:
Provide reasonable assurance that company objectives and goals are achieved and problems and surprises are minimized.
Achieve its financial and performance targets.
Assess risks continuously and identify steps to take and resources to allocate to overcome or mitigate risk.
Avoid adverse publicity and damage to the entity’s reputation.
CONTROL FRAMEWORKS
ERM defines risk management as:
A process effected by an entity’s board of directors, management, and other personnel
Applied in strategy setting and across the enterprise
To identify potential events that may affect the entity
And manage risk to be within its risk appetite
In order to provide reasonable assurance of the achievement of entity objectives.
CONTROL FRAMEWORKS
Basic principles behind ERM:
Companies are formed to create value for owners.
Management must decide how much uncertainty they will accept.
Uncertainty can result in:
Risk
The possibility that something will happen to:
Adversely affect the ability to create value; or
Erode existing value.
CONTROL FRAMEWORKS
Basic principles behind ERM:
Companies are formed to create value for owners.
Management must decide how much uncertainty they will accept.
Uncertainty can result in:
Risk
Opportunity
The possibility that something will happen to positively affect the ability to create or preserve value.
CONTROL FRAMEWORKS
The framework should help management manage uncertainty and its associated risk to build and preserve value.
To maximize value, a company must balance its growth and return objectives and risks with efficient and effective use of company resources.
CONTROL FRAMEWORKS
COSO developed a model to illustrate the elements of ERM.
CONTROL FRAMEWORKS
Columns at the top represent the four types of objectives that management must meet to achieve company goals.
Strategic objectives
Strategic objectives are high-level goals that are aligned with and support the company’s mission.
CONTROL FRAMEWORKS
Columns at the top represent the four types of objectives that management must meet to achieve company goals.
Strategic objectives
Operations objectives
Operations objectives deal with effectiveness and efficiency of company operations, such as:
Performance and profitability goals
Safeguarding assets
CONTROL FRAMEWORKS
Columns at the top represent the four types of objectives that management must meet to achieve company goals.
Strategic objectives
Operations objectives
Reporting objectives
Reporting objectives help ensure the accuracy, completeness, and reliability of internal and external company reports of both a financial and non-financial nature.
Improve decision-making and monitor company activities and performance more efficiently.
CONTROL FRAMEWORKS
Columns at the top represent the four types of objectives that management must meet to achieve company goals.
Strategic objectives
Operations objectives
Reporting objectives
Compliance objectives
Compliance objectives help the company comply with applicable laws and regulations.
External parties often set the compliance rules.
Companies in the same industry often have similar concerns in this area.
CONTROL FRAMEWORKS
ERM can provide reasonable assurance that reporting and compliance objectives will be achieved because companies have control over them.
However, strategic and operations objectives are sometimes at the mercy of external events that the company can’t control.
Therefore, in these areas, the only reasonable assurance the ERM can provide is that management and directors are informed on a timely basis of the progress the company is making in achieving them.
CONTROL FRAMEWORKS
Columns on the right represent the company’s units:
Entire company
CONTROL FRAMEWORKS
Columns on the right represent the company’s units:
Entire company
Division
CONTROL FRAMEWORKS
Columns on the right represent the company’s units:
Entire company
Division
Business unit
CONTROL FRAMEWORKS
Columns on the right represent the company’s units:
Entire company
Division
Business unit
Subsidiary
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
The tone or culture of the company.
Provides discipline and structure and is the foundation for all other components.
Essentially the same as control environment in the COSO internal control framework.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Ensures that management implements a process to formulate strategic, operations, reporting, and compliance objectives that support the company’s mission and are consistent with the company’s tolerance for risk.
Strategic objectives are set first as a foundation for the other three.
The objectives provide guidance to companies as they identify risk-creating events and assess and respond to those risks.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Requires management to identify events that may affect the company’s ability to implement its strategy and achieve its objectives.
Management must then determine whether these events represent:
Risks (negative-impact events requiring assessment and response); or
Opportunities (positive-impact events that influence strategy and objective-setting processes).
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Risk assessment
Identified risks are assessed to determine how to manage them and how they affect the company’s ability to achieve its objectives.
Qualitative and quantitative methods are used to assess risks individually and by category in terms of:
Likelihood
Positive and negative impact
Effect on other organizational units
Risks are analyzed on an inherent and a residual basis.
Corresponds to the risk assessment element in COSO’s internal control framework.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Risk assessment
Risk response
Management aligns identified risks with the company’s tolerance for risk by choosing to:
Avoid
Reduce
Share
Accept
Management takes an entity-wide or portfolio view of risks in assessing the likelihood of the risks, their potential impact, and costs-benefits of alternate responses.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Risk assessment
Risk response
Control activities
To implement management’s risk responses, control policies and procedures are established and implemented throughout the various levels and functions of the organization.
Corresponds to the control activities element in the COSO internal control framework.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Risk assessment
Risk response
Control activities
Information and communication
Information about the company and ERM components must be identified, captured, and communicated so employees can fulfill their responsibilities.
Information must be able to flow through all levels and functions in the company as well as flowing to and from external parties.
Employees should understand their role and importance in ERM and how these responsibilities relate to those of others.
Has a corresponding element in the COSO internal control framework.
CONTROL FRAMEWORKS
The horizontal rows are eight related risk and control components, including:
Internal environment
Objective setting
Event identification
Risk assessment
Risk response
Control activities
Information and communication
Monitoring
ERM processes must be monitored on an ongoing basis and modified as needed.
Accomplished with ongoing management activities and separate evaluations.
Deficiencies are reported to management.
Corresponding module in COSO internal control framework.
CONTROL FRAMEWORKS
The ERM model is three-dimensional.
Means that each of the eight risk and control elements are applied to the four objectives in the entire company and/or one of its subunits.
CONTROL FRAMEWORKS
ERM Framework Vs. the Internal Control Framework
The internal control framework has been widely adopted as the principal way to evaluate internal controls as required by SOX. However, there are issues with it.
It has too narrow of a focus.
Examining controls without first examining purposes and risks of business processes provides little context for evaluating the results.
Makes it difficult to know:
Which control systems are most important.
Whether they adequately deal with risk.
Whether important control systems are missing.
CONTROL FRAMEWORKS
ERM Framework Vs. the Internal Control Framework
The internal control framework has been widely adopted as the principal way to evaluate internal controls as required by SOX. However, there are issues with it.
It has too narrow of a focus.
Focusing on controls first has an inherent bias toward past problems and concerns.
May contribute to systems with many controls to protect against risks that are no longer important.
CONTROL FRAMEWORKS
These issues led to COSO’s development of the ERM framework.
Takes a risk-based, rather than controls-based, approach to the organization.
Oriented toward future and constant change.
Incorporates rather than replaces COSO’s internal control framework and contains three additional elements:
Setting objectives.
Identifying positive and negative events that may affect the company’s ability to implement strategy and achieve objectives.
Developing a response to assessed risk.
CONTROL FRAMEWORKS
Controls are flexible and relevant because they are linked to current organizational objectives.
ERM also recognizes more options than simply controlling risk, which include accepting it, avoiding it, diversifying it, sharing it, or transferring it.
CONTROL FRAMEWORKS
Over time, ERM will probably become the most widely adopted risk and control model.
Consequently, its eight components are the topic of the remainder of the chapter.
INTERNAL ENVIRONMENT
The most critical component of the ERM and the internal control framework.
Is the foundation on which the other seven components rest.
Influences how organizations:
Establish strategies and objectives
Structure business activities
Identify, access, and respond to risk
A deficient internal control environment often results in risk management and control breakdowns.
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Management’s Philosophy, Operating Style, and Risk Appetite
An organization’s management has shared beliefs and attitudes about risk.
That philosophy affects everything the organization does, long- and short-term, and affects their communications.
Companies also have a risk appetite , which is the amount of risk a company is willing to accept to achieve its goals and objectives.
That appetite needs to be in alignment with company strategy.
INTERNAL ENVIRONMENT
The more responsible management’s philosophy and operating style, the more likely employees will behave responsibly.
This philosophy must be clearly communicated to all employees; it is not enough to give lip service.
Management must back up words with actions; if they show little concern for internal controls, then neither will employees.
INTERNAL ENVIRONMENT
This component can be assessed by asking questions such as:
Does management take undue business risks or assess potential risks and rewards before acting?
Does management attempt to manipulate performance measures such as net income?
Does management pressure employees to achieve results regardless of methods or do they demand ethical behavior?
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
The Board of Directors
An active and involved board of directors plays an important role in internal control.
They should:
Oversee management
Scrutinize management’s plans, performance, and activities
Approve company strategy
Review financial results
Annually review the company’s security policy
Interact with internal and external auditors
INTERNAL ENVIRONMENT
Directors should possess management, technical, or other expertise, knowledge, or experience, as well as a willingness to advocate for shareholders.
At least a majority should be independent, outside directors not affiliated with the company or any of its subsidiaries.
INTERNAL ENVIRONMENT
Public companies must have an audit committee , composed entirely of independent, outside directors.
The audit committee oversees:
The company’s internal control structure;
Its financial reporting process;
Its compliance with laws, regulations, and standards.
Works with the corporation’s external and internal auditors.
Hires, compensates, and oversees the auditors.
Auditors report all critical accounting policies and practices to the audit committee.
Provides an independent review of management’s actions.
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Commitment to Integrity, Ethical Values, and Competence
Management must create an organizational culture that stresses integrity and commitment to both ethical values and competence.
Ethical standards of behavior make for good business.
Tone at the top is everything.
Employees will watch the actions of the CEO, and the message of those actions (good or bad) will tend to permeate the organization.
INTERNAL ENVIRONMENT
Companies can endorse integrity as a basic operating principle by actively teaching and requiring it.
Management should:
Make it clear that honest reports are more important than favorable ones.
Management should avoid:
Unrealistic expectations, incentives or temptations.
Attitude of earnings or revenue at any price.
Overly aggressive sales practices.
Unfair or unethical negotiation practices.
Implied kickback offers.
Excessive bonuses.
Bonus plans with upper and lower cutoffs.
INTERNAL ENVIRONMENT
Management should not assume that employees would always act honestly.
Consistently reward and encourage honesty.
Give verbal labels to honest and dishonest acts.
The combination of these two will produce more consistent moral behavior.
INTERNAL ENVIRONMENT
Management should develop clearly stated policies that explicitly describe honest and dishonest behaviors, often in the form of a written code of conduct.
In particular, such a code would cover issues that are uncertain or unclear.
Dishonesty often appears when situations are gray and employees rationalize the most expedient action as opposed to making a right vs. wrong choice.
INTERNAL ENVIRONMENT
SOX only requires a code of ethics for senior financial management. However, the ACFE suggests that companies create a code of conduct for all employees:
Should be written at a fifth-grade level.
Should be reviewed annually with employees and signed.
This approach helps employees keep themselves out of trouble.
Helps the company if they need to take legal action against the employee.
INTERNAL ENVIRONMENT
Management should require employees to report dishonest, illegal, or unethical behavior and discipline employees who knowingly fail to report.
Reports of dishonest acts should be thoroughly investigated.
Those found guilty should be dismissed.
Prosecution should be undertaken when possible, so that other employees are clear about consequences.
Companies must make a commitment to competence.
Begins with having competent employees.
Varies with each job but is a function of knowledge, experience, training, and skills.
INTERNAL ENVIRONMENT
The levers of control, particularly beliefs and boundaries systems, can be used to create the kind of commitment to integrity an organization wants.
Requires more than lip service and signing forms.
Must be systems in which top management actively participates in order to:
Demonstrate the importance of the system.
Create buy-in and a team spirit.
INTERNAL ENVIRONMENT
Management should require employees to report dishonest, illegal, or unethical behavior and discipline employees who knowingly fail to report.
Reports of dishonest acts should be thoroughly investigated.
Those found guilty should be dismissed.
Prosecution should be undertaken when possible, so that other employees are clear about consequences.
INTERNAL ENVIRONMENT
Companies must make a commitment to competence.
Begins with having competent employees.
Varies with each job but is a function of knowledge, experience, training, and skills.
INTERNAL ENVIRONMENT
The levers of control, particularly beliefs and boundary systems, can be used to create the kind of commitment to integrity an organization wants.
Requires more than lip service and signing forms.
Must be systems in which top management actively participates in order to:
Demonstrate the importance of the system.
Create buy-in and a team spirit.
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Organizational Structure
A company’s organizational structure defines its lines of authority, responsibility, and reporting.
Provides the overall framework for planning, directing, executing, controlling, and monitoring its operations.
INTERNAL ENVIRONMENT
Important aspects or organizational structure:
Degree of centralization or decentralization.
Assignment of responsibility for specific tasks.
Direct-reporting relationships or matrix structure
Organization by industry, product, geographic location, marketing network
How the responsibility allocation affects management’s information needs
Organization of accounting and IS functions
Size and nature of company activities
INTERNAL ENVIRONMENT
Statistically fraud occurs more frequently in organizations with complex structures
The structures may unintentionally impede communication and clear assignment of responsibility, making fraud easier to commit and conceal; or
The structure may be intentionally complex to facilitate the fraud.
INTERNAL ENVIRONMENT
In today’s business world, the hierarchical organizations with many layers of management are giving way to flatter organizations with self-directed work teams.
Team members are empowered to make decisions without multiple layers of approvals.
Emphasis is on continuous improvement rather than on regular evaluations.
These changes have a significant impact on the nature and type of controls needed.
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Methods of Assigning Authority and Responsibility
Management should make sure:
Employees understand the entity’s objectives
Authority and responsibility for business objectives is assigned to specific departments and individuals
Ownership of responsibility encourages employees to take initiative in solving problems and holds them accountable for achieving objectives.
Management:
Must be sure to identify who is responsible for the IS security policy.
Should monitor results so decisions can be reviewed and, if necessary, overruled.
INTERNAL ENVIRONMENT
Authority and responsibility are assigned through:
Formal job descriptions
Employee training
Operating plans, schedules, and budgets
Codes of conduct that define ethical behavior, acceptable practices, regulatory requirements, and conflicts of interest
Written policies and procedures manuals (a good job reference and job training tool) which covers:
Proper business practices
Knowledge and experience needed by key personnel
Resources provided to carry out duties
Policies and procedures for handling particular transactions
The organization’s chart of accounts
Sample copies of forms and documents
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
Human Resources Standards
Employees are both the company’s greatest control strength and the greatest control weakness.
Organizations can implement human resource policies and practices with respect to hiring, training, compensating, evaluating, counseling, promoting, and discharging employees that send messages about the level of competence and ethical behavior required.
Policies on working conditions, incentives, and career advancement can powerfully encourage efficiency and loyalty and reduce the organization’s vulnerability.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Hiring
Should be based on educational background, relevant work experience, past achievements, honesty and integrity, and how well candidates meet written job requirements.
Employees should undergo a formal, in-depth employment interview.
Resumes, reference letters, and thorough background checks are critical.
INTERNAL ENVIRONMENT
Background checks can involve:
Verifying education and experience
Talking with references
Checking for criminal records, credit issues, and other publicly available data.
Note that you must have the employee’s or candidate’s written permission to conduct a background check, but that permission does not need to have an expiration date.
Background checks are important because recent studies show that about 50% of resumes have been falsified or embellished.
INTERNAL ENVIRONMENT
Sometimes professional firms are hired to do the background checks because applicants are becoming more aggressive in their deceptions.
Some get phony degrees from online “diploma mills.”
A Pennsylvania district attorney recently filed suit against a Texas “university” for issuing an MBA to the DA’s 6-year-old black cat.
Others actually hack (or hire someone to hack) into the systems of universities to create or alter transcripts and other academic data.
No employee should be exempted from background checks. Anyone from the custodian to the company president is capable of committing fraud, sabotage, etc
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Compensating
Employees should be paid a fair and competitive wage.
Poorly compensated employees are more likely to feel the resentment and financial pressures that lead to fraud.
Appropriate incentives can motivate and reinforce outstanding performance.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Policies on Training
Training programs should familiarize new employees with:
Their responsibilities.
Expected performance and behavior.
Company policies, procedures, history, culture, and operating style.
Training needs to be ongoing, not just one-time.
Companies who shortchange training are more likely to experience security breaches and fraud.
INTERNAL ENVIRONMENT
Many believe employee training and education are the most important elements of fraud prevention and security programs.
Fraud is less likely to occur when employees believe security is everyone’s business.
An ideal corporate culture exists when:
Employees are proud of their company and protective of its assets.
They believe fraud hurts everyone and that they therefore have a responsibility to report it.
INTERNAL ENVIRONMENT
These cultures do not just happen. They must be created, taught, and practiced, and the following training should be provided:
Fraud awareness
Employees should be aware of fraud’s prevalence and dangers, why people do it, and how to deter and detect it.
Ethical considerations
The company should promote ethical standards in its practice and its literature.
Acceptable and unacceptable behavior should be defined and labeled, leaving as little gray area as possible.
INTERNAL ENVIRONMENT
Punishment for fraud and unethical behavior.
Employees should know the consequences (e.g., reprimand, dismissal, prosecution) of bad behavior.
Should be disseminated as a consequence rather than a threat.
EXAMPLE: “Using a computer to steal or commit fraud is a federal crime, and anyone doing so faces immediate dismissal and/or prosecution.”
The company should display notices of program and data ownership and advise employees of the penalties of misuse.
INTERNAL ENVIRONMENT
Training can take place through:
Informal discussions
Formal meetings
Periodic memos
Written guidelines
Codes of ethics
Circulating reports of unethical behavior and its consequences
Promoting security and fraud training programs
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Evaluating and promoting
Do periodic performance appraisals to help employees understand their strengths and weaknesses.
Base promotions on performance and qualifications.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Discharging
Fired employees are disgruntled employees.
Disgruntled employees are more likely to commit a sabotage or fraud against the company.
Employees who are terminated (whether voluntary or involuntary) should be removed from sensitive jobs immediately and denied access to information systems.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Managing disgruntled employees
Disgruntled employees may be isolated and/or unhappy, but are much likelier fraud candidates than satisfied employees.
The organization can try to reduce the employee’s pressures through grievance channels and counseling.
Difficult to do because many employees feel that seeking counseling will stigmatize them in their jobs.
Disgruntled employees should not be allowed to continue in jobs where they could harm the organization.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Vacations and rotation of duties
Some fraud schemes, such as lapping and kiting, cannot continue without the constant attention of the perpetrator.
Mandatory vacations or rotation of duties can prevent these frauds or lead to early detection.
These measures will only be effective if someone else is doing the job while the usual employee is elsewhere.
INTERNAL ENVIRONMENT
The following policies and procedures are important:
Hiring
Compensating
Training
Evaluating and promoting
Discharging
Managing disgruntled employees
Vacations and rotation of duties
Confidentiality insurance and fidelity bonds
INTERNAL ENVIRONMENT
Confidentiality agreements and fidelity bond insurance
Employees, suppliers, and contractors should be required to sign and abide by nondisclosure or confidentiality agreements.
Key employees should have fidelity bond insurance coverage to protect the company against losses from fraudulent acts by those employees.
INTERNAL ENVIRONMENT
In addition to the preceding policies, the company should seek prosecution and incarceration of hackers and fraud perpetrators
Most fraud cases and hacker attacks go unreported. They are not prosecuted for several reasons.
Companies fear:
Public relations nightmares
Copycat attacks
But unreported fraud and intrusions create a false sense of security.
INTERNAL ENVIRONMENT
Law enforcement officials and courts are busy with violent crimes and may regard teen hacking as “childish pranks.”
Fraud is difficult, costly, and time-consuming to investigate and prosecute.
Law enforcement officials, lawyers, and judges often lack the computer skills needed to investigate, prosecute, and evaluate computer crimes.
When cases are prosecuted and a conviction obtained, penalties are often very light. Judges often regard the perps as “model citizens.”
INTERNAL ENVIRONMENT
Internal environment consists of the following:
Management’s philosophy, operating style, and risk appetite
The board of directors
Commitment to integrity, ethical values, and competence
Organizational structure
Methods of assigning authority and responsibility
Human resource standards
External influences
INTERNAL ENVIRONMENT
External influences
External influences that affect the control environment include requirements imposed by:
FASB
PCAOB
SEC
Insurance commissions
Regulatory agencies for banks, utilities, etc.
OBJECTIVE SETTING
Objective setting is the second ERM component.
It must precede many of the other six components.
For example, you must set objectives before you can define events that affect your ability to achieve objectives
OBJECTIVE SETTING
Top management, with board approval, must articulate why the company exists and what it hopes to achieve.
Often referred to as the corporate vision or mission.
Uses the mission statement as a base from which to set corporate objectives.
The objectives:
Need to be easy to understand and measure.
Should be prioritized.
Should be aligned with the company’s risk appetite.
OBJECTIVE SETTING
Objectives set at the corporate level are linked to and integrated with a cascading series of sub-objectives in the various sub-units.
For each set of objectives:
Critical success factors (what has to go right) must be defined.
Performance measures should be established to determine whether the objectives are met.
OBJECTIVE SETTING
Objective-setting process proceeds as follows:
First, set strategic objectives, the high-level goals that support the company’s mission and create value for shareholders.
To meet these objectives, identify alternative ways of accomplishing them.
For each alternative, identify and assess risks and implications.
Formulate a corporate strategy.
Then set operations, compliance, and reporting objectives.
OBJECTIVE SETTING
As a rule of thumb:
The mission and strategic objectives are stable.
The strategy and other objectives are more dynamic:
Must be adapted to changing conditions.
Must be realigned with strategic objectives.
OBJECTIVE SETTING
Operations objectives:
Are a product of management preferences, judgments, and style
Vary significantly among entities:
One may adopt technology; another waits until the bugs are worked out.
Are influenced by and must be relevant to the industry, economic conditions, and competitive pressures.
Give clear direction for resource allocation—a key success factor.
OBJECTIVE SETTING
Compliance and reporting objectives:
Many are imposed by external entities, e.g.:
Reports to IRS or to EPA
Financial reports that comply with GAAP
A company’s reputation can be impacted significantly (for better or worse) by the quality of its compliance.
EVENT IDENTIFICATION
Events are:
Incidents or occurrences that emanate from internal or external sources
That affect implementation of strategy or achievement of objectives.
Impact can be positive, negative, or both.
Events can range from obvious to obscure.
Effects can range from inconsequential to highly significant.
EVENT IDENTIFICATION
By their nature, events represent uncertainty:
Will they occur?
If so, when?
And what will the impact be?
Will they trigger another event?
Will they happen individually or concurrently?
EVENT IDENTIFICATION
Management must do its best to anticipate all possible events—positive or negative—that might affect the company:
Try to determine which are most and least likely.
Understand the interrelationships of events.
COSO identified many internal and external factors that could influence events and affect a company’s ability to implement strategy and achieve objectives.
EVENT IDENTIFICATION
Some of these factors include:
External factors:
Economic factors
Availability of capital; lower or higher costs of capital
Lower barriers to entry, resulting in new competition
Price movements up or down
Ability to issue credit and possibility of default
Concentration of competitors, customers, or vendors
Presence or absence of liquidity
Movements in the financial markets or currency fluctuations
Rising or lowering unemployment rates
Mergers or acquisitions
Potential regulatory, contractual, or criminal legal liability
EVENT IDENTIFICATION
Some of these factors include:
External factors:
Economic factors
Natural environment
Natural disasters such as fires, floods, or earthquakes
Emissions and waste
Energy restrictions or shortages
Restrictions limiting development
EVENT IDENTIFICATION
Some of these factors include:
External factors:
Economic factors
Natural environment
Political factors
Election of government officials with new agendas
New laws and regulations
Public policy, including higher or lower taxes
Regulation affecting the company’s ability to compete
EVENT IDENTIFICATION
Some of these factors include:
External factors:
Economic factors
Natural environment
Political factors
Social factors
Changing demographics, social mores, family structures, and work/life priorities
Consumer behavior that changes demand for products and services or creates new buying opportunities
Corporate citizenship
Privacy
Terrorism
Human resource issues causing production shortages or stoppages
EVENT IDENTIFICATION
Some of these factors include:
External factors:
Economic factors
Natural environment
Political factors
Social factors
Technological factors
New e-business technologies that lower infrastructure costs or increase demand for IT-based services
Emerging technology
Increased or decreased availability of data
Interruptions or down time caused by external parties
EVENT IDENTIFICATION
Some of these factors include:
Internal factors:
Infrastructure
Inadequate access or poor allocation of capital
Availability and capability of company assets
Complexity of systems
EVENT IDENTIFICATION
Some of these factors include:
Internal factors:
Infrastructure
Personnel
Employee skills and capability
Employees acting dishonestly or unethically
Workplace accidents, health or safety concerns
Strikes or expiration of labor agreements
EVENT IDENTIFICATION
Some of these factors include:
Internal factors:
Infrastructure
Personnel
Process
Process modification without proper change management procedures
Poorly designed processes
Process execution errors
Suppliers cannot deliver quality goods on time
EVENT IDENTIFICATION
Some of these factors include:
Internal factors:
Infrastructure
Personnel
Process
Technology
Insufficient capacity to handle peak IT usages
Security breaches
Data or system unavailability from internal factors
Inadequate data integrity
Poor systems selection/development
Inadequately maintained systems
EVENT IDENTIFICATION
Lists can help management identify factors, evaluate their importance, and examine those that can affect objectives.
Identifying events at the activity and entity levels allows companies to focus their risk assessment on major business units or functions and align their risk tolerance and risk appetite.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Often produced by special software that can tailor lists to an industry, activity, or process.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Perform an internal analysis
An internal committee analyzes events, contacting appropriate insiders and outsiders for input.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Perform an internal analysis
Monitor leading events and trigger points
Appropriate transactions, activities, and events are monitored and compared to predefined criteria to determine when action is needed.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Perform an internal analysis
Monitor leading events and trigger points
Conduct workshops and interviews
Employee knowledge and expertise is gathered in structured discussions or individual interviews.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Perform an internal analysis
Monitor leading events and trigger points
Conduct workshops and interviews
Perform data mining and analysis
Examine data on prior events to identify trends and causes that help identify possible events.
EVENT IDENTIFICATION
Companies usually use two or more of the following techniques together to identify events:
Use comprehensive lists of potential events
Perform an internal analysis
Monitor leading events and trigger points
Conduct workshops and interviews
Perform data mining and analysis
Analyze processes
Analyze internal and external factors that affect inputs, processes, and outputs to identify events that might help or hinder the process.
RISK ASSESSMENT AND RISK RESPONSE
The fourth and fifth components of COSO’s ERM model are risk assessment and risk response.
COSO indicates there are two types of risk:
Inherent risk
The risk that exists before management takes any steps to control the likelihood or impact of a risk.
RISK ASSESSMENT AND RISK RESPONSE
The fourth and fifth components of COSO’s ERM model are risk assessment and risk response.
COSO indicates there are two types of risk:
Inherent risk
Residual risk
The risk that remains after management implements internal controls or some other form of response to risk.
RISK ASSESSMENT AND RISK RESPONSE
Companies should:
Assess inherent risk
Develop a response
Then assess residual risk
The ERM model indicates four ways to respond to risk:
Reduce it
The most effective way to reduce the likelihood and impact of risk is to implement an effective system of internal controls.
RISK ASSESSMENT AND RISK RESPONSE
Companies should:
Assess inherent risk
Develop a response
Then assess residual risk
The ERM model indicates four ways to respond to risk:
Reduce it
Accept it
Don’t act to prevent or mitigate it.
RISK ASSESSMENT AND RISK RESPONSE
Companies should:
Assess inherent risk
Develop a response
Then assess residual risk
The ERM model indicates four ways to respond to risk:
Reduce it
Accept it
Share it
Transfer some of it to others via activities such as insurance, outsourcing, or hedging.
RISK ASSESSMENT AND RISK RESPONSE
Companies should:
Assess inherent risk
Develop a response
Then assess residual risk
The ERM model indicates four ways to respond to risk:
Reduce it
Accept it
Share it
Avoid it
Don’t engage in the activity that produces it.
May require:
Sale of a division
Exiting a product line
Canceling an expansion plan
RISK ASSESSMENT AND RISK RESPONSE
Accountants:
Help management design effective controls to reduce inherent risk
Evaluate internal control systems to ensure they are operating effectively
Assess and reduce inherent risk using the risk assessment and response strategy
RISK ASSESSMENT AND RISK RESPONSE
Event Identification
The first step in risk assessment and response strategy is event identification, which we have already discussed.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Estimate Likelihood and Impact
Some events pose more risk because they are more probable than others.
Some events pose more risk because their dollar impact would be more significant.
Likelihood and impact must be considered together:
If either increases, the materiality of the event and the need to protect against it rises.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Identify Controls
Management must identify one or more controls that will protect the company from each event.
In evaluating benefits of each control procedure, consider effectiveness and timing.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
All other factors equal:
A preventive control is better than a detective one.
However, if preventive controls fail, detective controls are needed to discover the problem, and corrective controls are needed to recover.
Consequently, the three complement each other, and a good internal control system should have all three.
Similarly, a company should use all four levers of control.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Estimate Costs and Benefits
It would be cost-prohibitive to create an internal control system that provided foolproof protection against all events.
Also, some controls negatively affect operational efficiency, and too many controls can make it very inefficient.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
The benefits of an internal control procedure must exceed its costs.
Benefits can be hard to quantify, but include:
Increased sales and productivity
Reduced losses
Better integration with customers and suppliers
Increased customer loyalty
Competitive advantages
Lower insurance premiums
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Costs are usually easier to measure than benefits.
Primary cost is personnel, including:
Time to perform control procedures
Costs of hiring additional employees to effectively segregate duties
Costs of programming controls into a system
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Other costs of a poor control system include:
Lost sales
Lower productivity
Drop in stock price if security problems arise
Shareholder or regulator lawsuits
Fines and penalties imposed by governmental agencies
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
The expected loss related to a risk is measured as:
Expected loss = impact x likelihood
The value of a control procedure is the difference between:
Expected loss with control procedure
Expected loss without it
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Determine Cost-Benefit Effectiveness
After estimating benefits and costs, management determines if the control is cost beneficial, i.e., is the cost of implementing a control procedure less than the change in expected loss that would be attributable to the change?
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
In evaluating costs and benefits, management must consider factors other than those in the expected benefit calculation.
If an event threatens an organization’s existence, it may be worthwhile to institute controls even if costs exceed expected benefits.
The additional cost can be viewed as a catastrophic loss insurance premium.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Let’s go through an example:
Hobby Hole is trying to decide whether to install a motion detector system in its warehouse to reduce the probability of a catastrophic theft.
A catastrophic theft could result in losses of $800,000.
Local crime statistics suggest that the probability of a catastrophic theft at Hobby Hole is 12%.
Companies with motion detectors only have about a .5% probability of catastrophic theft.
The present value of purchasing and installing a motion detector system and paying future security costs is estimated to be about $43,000.
Should Hobby Hole install the motion detectors?
Expected Loss without control procedure = $800,000 x .12 = $96,000.
Expected loss with control procedure = $800,000 x .005 = $4,000.
Estimated value of control procedure = $96,000 - $4,000 = $92,000.
Estimated cost of control procedure = $43,000 (given).
Benefits exceed costs by $92,000 - $43,000 = $49,000 .
In this case, Hobby Hole should probably install the motion detectors.
RISK ASSESSMENT AND RISK RESPONSE
Implement the Control or Avoid, Share, or Accept the Risk
When controls are cost effective, they should be implemented so risk can be reduced.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
RISK ASSESSMENT AND RISK RESPONSE
Risks that are not reduced must be accepted, shared, or avoided.
If the risk is within the company’s risk tolerance, they will typically accept the risk.
A reduce or share response is used to bring residual risk into an acceptable risk tolerance range.
An avoid response is typically only used when there is no way to cost-effectively bring risk into an acceptable risk tolerance range.
Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Reduce risk by implementing set of controls to guard against threat Is it cost-beneficial to protect system Avoid, share, or accept risk Yes No
CONTROL ACTIVITIES
The sixth component of COSO’s ERM model.
Control activities are policies, procedures, and rules that provide reasonable assurance that management’s control objectives are met and their risk responses are carried out.
CONTROL ACTIVITIES
It is management’s responsibility to develop a secure and adequately controlled system.
Controls are much more effective when built in on the front end.
Consequently, systems analysts, designers, and end users should be involved in designing adequate computer-based control systems.
Management must also establish a set of procedures to ensure control compliance and enforcement.
Usually the purview of the information security officer and the operations staff.
CONTROL ACTIVITIES
It is critical that controls be in place during the year-end holiday season. A disproportionate amount of computer fraud and security break-ins occur during this time because:
More people are on vacation and fewer around to mind the store.
Students are not tied up with school.
Counterculture hackers may be lonely.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Proper Authorization of Transactions and Activities
Management lacks the time and resources to supervise each employee activity and decision.
Consequently, they establish policies and empower employees to perform activities within policy.
This empowerment is called authorization and is an important part of an organization’s control procedures.
CONTROL ACTIVITIES
Authorizations are often documented by signing initializing, or entering an authorization code.
Computer systems can record digital signatures as a means of signing a document.
Employees who process transactions should verify the presence of the appropriate authorizations.
Auditors review transactions for proper authorization, as their absence indicates a possible control problem.
CONTROL ACTIVITIES
Typically at least two levels of authorization:
General authorization
Management authorizes employees to handle routine transactions without special approval.
Special authorization
For activities or transactions that are of significant consequences, management review and approval is required.
Might apply to sales, capital expenditures, or write-offs over a particular dollar limit.
Management should have written policies for both types of authorization and for all types of transactions.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Segregation of Duties
Good internal control requires that no single employee be given too much responsibility over business transactions or processes.
An employee should not be in a position to commit and conceal fraud or unintentional errors.
Segregation of duties is discussed in two sections:
Segregation of accounting duties
Segregation of duties within the systems function
CONTROL ACTIVITIES
Segregation of Duties
Good internal control requires that no single employee be given too much responsibility over business transactions or processes.
An employee should not be in a position to commit and conceal fraud or unintentional errors.
Segregation of duties is discussed in two sections:
Segregation of accounting duties
Segregation of duties within the systems function
CONTROL ACTIVITIES
To learn a little about segregation of duties, let’s first meet Bill.
CONTROL ACTIVITIES
Bill has charge of a pile of the organization’s money—let’s say $1,000.
CONTROL ACTIVITIES
Bill also keeps the books for that money.
Ledger $1,000
CONTROL ACTIVITIES
Bill has a date tonight, and he’s a little desperate to impress that special someone, so he takes $100 of the cash. (Thinks he’s only borrowing it, you know.)
Ledger $1,000
CONTROL ACTIVITIES
Bill has a date tonight, and he’s a little desperate to impress that special someone, so he takes $100 of the cash. (Thinks he’s only borrowing it, you know.)
Ledger $1,000
CONTROL ACTIVITIES
Bill also records an entry in the books to show that $100 was spent for some “legitimate” purpose. Now the balance in the books is $900.
Ledger $1,000
CONTROL ACTIVITIES
How will Bill ever get caught at his theft?
Ledger $900
CONTROL ACTIVITIES
Now let’s change the story. Bill has charge of the pile of cash.
CONTROL ACTIVITIES
But Mary keeps the books.
This arrangement is a form of segregation of duties.
Ledger $1,000
CONTROL ACTIVITIES
Bill gets in a pinch again and takes $100 of the organization’s cash.
Ledger $1,000
CONTROL ACTIVITIES
How will Bill get caught?
Ledger $1,000
CONTROL ACTIVITIES
Segregation of Accounting Duties
Effective segregation of accounting duties is achieved when the following functions are separated:
Authorization —approving transactions and decisions.
Recording —Preparing source documents; maintaining journals, ledgers, or other files; preparing reconciliations; and preparing performance reports.
Custody —Handling cash, maintaining an inventory storeroom, receiving incoming customer checks, writing checks on the organization’s bank account.
If any two of the preceding functions are the responsibility of one person, then problems can arise.
CONTROL ACTIVITIES
CUSTODIAL FUNCTIONS
Handling cash
Handling inventories, tools, or fixed assets
Writing checks
Receiving checks in mail
AUTHORIZATION FUNCTIONS
Authorization of transactions
RECORDING FUNCTIONS
Preparing source documents
Maintaining journals, ledgers, or other files
Preparing reconciliations
Preparing performance reports
EXAMPLE OF PROBLEM: A person who has custody of cash receipts and the recording for those receipts can steal some of the cash and falsify accounts to conceal the theft.
SOLUTION: The pink fence (segregation of custody and recording) prevents employees from falsifying records to conceal theft of assets entrusted to them.
CONTROL ACTIVITIES
CUSTODIAL FUNCTIONS
Handling cash
Handling inventories, tools, or fixed assets
Writing checks
Receiving checks in mail
AUTHORIZATION FUNCTIONS
Authorization of transactions
RECORDING FUNCTIONS
Preparing source documents
Maintaining journals, ledgers, or other files
Preparing reconciliations
Preparing performance reports
EXAMPLE OF PROBLEM: A person who has custody of checks for transactions that he has authorized can authorize fictitious transactions and then steal the payments.
SOLUTION: The green fence (segregation of custody and authorization) prevents employees from authorizing fictitious or inaccurate transactions as a means of concealing a theft.
CONTROL ACTIVITIES
CUSTODIAL FUNCTIONS
Handling cash
Handling inventories, tools, or fixed assets
Writing checks
Receiving checks in mail
AUTHORIZATION FUNCTIONS
Authorization of transactions
RECORDING FUNCTIONS
Preparing source documents
Maintaining journals, ledgers, or other files
Preparing reconciliations
Preparing performance reports
EXAMPLE OF PROBLEM: A person who can authorize a transaction and keep records related to the transactions can authorize and record fictitious payments that might, for example, be sent to the employee’s home address or the address of a shell company he creates.
SOLUTION: The purple fence (segregation of recording and authorization) prevents employees from falsifying records to cover up inaccurate or false transactions that were inappropriately authorized.
CONTROL ACTIVITIES
In a system that incorporates an effective separation of duties, it should be difficult for any single employee to commit embezzlement successfully.
But when two or more people collude , then segregation of duties becomes impotent and controls are overridden.
CONTROL ACTIVITIES
If this happens . . .
Ledger $1,000
CONTROL ACTIVITIES
Then segregation of duties is out the window. Collusion overrides segregation.
Ledger $1,000
CONTROL ACTIVITIES
Employees can collude with other employees or with customers or vendors.
The most frequent form of employee/vendor collusions include:
Billing at inflated prices
Performing substandard work and receiving full payment
Payment for non-performance
Duplicate billings
Improperly funneling more work to or purchasing more goods from a colluding company
CONTROL ACTIVITIES
The most frequent form of employee/customer collusions include:
Unauthorized loans or insurance payments
Receipt of assets or services at unauthorized discount prices
Forgiveness of amounts owed
Unauthorized extension of due dates
CONTROL ACTIVITIES
Segregation of Duties
Good internal control requires that no single employee be given too much responsibility over business transactions or processes.
An employee should not be in a position to commit and conceal fraud or unintentional errors.
Segregation of duties is discussed in two sections:
Segregation of accounting duties
Segregation of duties within the systems function
CONTROL ACTIVITIES
Segregation of Duties Within the Systems Function
In a highly integrated information system, procedures once performed by separate individuals are combined.
Therefore, anyone who has unrestricted access to the computer, its programs, and live data could have the opportunity to perpetrate and conceal fraud.
To combat this threat, organizations must implement effective segregation of duties within the IS function.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Responsible for ensuring that the different parts of an information system operate smoothly and efficiently.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Ensures that all applicable devices are linked to the organization’s internal and external networks and that the networks operate continuously and properly.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Ensures that all aspects of the system are secure and protected from internal and external threats.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Manages changes to the organization’s information system to ensure they are made smoothly and efficiently and to prevent errors and fraud.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Record transactions, authorize data to be processed, and use system output.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Systems analysts
Help users determine their information needs and design systems to meet those needs.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Systems analysts
Programming
Use design provided by the systems analysts to write the computer programs for the information system.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Systems analysts
Programming
Computer operations
Run the software on the company’s computers.
Ensure that data are input properly, correctly processed, and needed output is produced.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Systems analysts
Programming
Computer operations
Information systems library
Maintains custody of corporate databases, files, and programs in a separate storage area.
CONTROL ACTIVITIES
Authority and responsibility must be divided clearly among the following functions:
Systems administration
Network management
Security management
Change management
Users
Systems analysts
Programming
Computer operations
Information systems library
Data control
Ensures that source data have been properly approved.
Monitors the flow of work through the computer.
Reconciles input and output.
Maintains a record of input errors to ensure their correction and resubmission.
Distributes system output.
CONTROL ACTIVITIES
It is important that different people perform the preceding functions.
Allowing a person to do two or more jobs exposes the company to the possibility of fraud.
In addition to adequate segregation of duties, organizations should ensure that the people who design, develop, implement, and operate the IS are qualified and well trained.
The same holds true for systems security personnel.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Project Development and Acquisition Controls
It’s important to have a formal, appropriate, and proven methodology to govern the development, acquisition, implementation, and maintenance of information systems and related technologies.
Should contain appropriate controls for:
Management review and approval
User involvement
Analysis
Design
Testing
Implementation
Conversion
Should make it possible for management to trace information inputs from source to disposition and vice versa (the audit trail).
CONTROL ACTIVITIES
Examples abound of poorly managed projects that have wasted large sums of money because certain basic principles of project management control were ignored.
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
A multi-year strategic plan should align the organization’s information system with its business strategies and show the projects that must be completed to achieve long-range goals.
Should address hardware, software, personnel, and infrastructure requirements.
Each year, the board and top management should prepare and approve the plan and its supporting budget.
Should be evaluated several times a year to ensure the organization can acquire needed components and maintain existing ones.
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
Project controls
A project development plan shows how a project will be completed, including:
Modules or tasks to be performed
Who will perform them
Anticipated completion dates
Project costs
Project milestones should be specified—points when progress is reviewed and actual completion times are compared to estimates
Each project should be assigned to a manager and team who are responsible for its success or failure.
At project completion, a project evaluation of the team members should be performed.
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
Project controls
Data processing schedule
Data processing tasks should be organized according to a schedule to maximize the use of scarce computer resources .
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
Project controls
Data processing schedule
Steering committee
A steering committee should guide and oversee systems development and acquisition.
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
Project controls
Data processing schedule
Steering committee
System performance measurements
To be evaluated properly, a system should be assessed with measures such as:
Throughput (output per unit of time)
Utilization (percent of time it is used productively)
Response time (how long it takes to respond)
CONTROL ACTIVITIES
The following basic principles of control should be applied to systems development in order to reduce the potential for cost overruns and project failure and to improve the efficiency and effectiveness of the IS:
Strategic master plan
Project controls
Data processing schedule
Steering committee
System performance measurements
Post-implementation review
A review should be performed after a development project is completed to determine if the anticipated benefits were achieved.
Helps control project development activities and encourage accurate and objective initial cost and benefit estimates.
CONTROL ACTIVITIES
To simplify and improve systems development, some companies hire a systems integrator—a vendor who uses common standards and manages the development effort using their own personnel and those of the client and other vendors.
Many companies rely on the integrator’s assurance that the project will be completed on time.
Unfortunately, the integrator is often wrong.
These third-party systems development projects are subject to the same cost overruns and missed deadlines as systems developed internally.
CONTROL ACTIVITIES
When using systems integrators, companies should adhere to the same basic rules used for project management of internal projects. In addition, they should:
Develop clear specifications
Before third parties bid, provide clear specifications, including:
Exact descriptions and definitions of the system
Explicit deadlines
Precise acceptance criteria
While it’s expensive to develop these specifications, it will save money in the end.
CONTROL ACTIVITIES
When using systems integrators, companies should adhere to the same basic rules used for project management of internal projects. In addition, they should:
Develop clear specifications
Monitor the systems integration project
A sponsors committee should monitor third-party development projects.
Established by the CIO and chaired by the project’s internal champion.
Should include department managers from all units that will use the system.
Should establish formal procedures for measuring and reporting project status.
Best approach is to:
Divide project into manageable tasks.
Assign responsibility for each task.
Meet on a regular basis (at least monthly) to review progress and assess quality.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Change Management Controls
Organizations constantly modify their information systems to reflect new business practices and take advantage of information technology advances.
Change management is the process of making sure that the changes do not negatively affect:
Systems reliability
Security
Confidentiality
Integrity
Availability
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Design and Use of Adequate Documents and Records
Proper design and use of documents and records helps ensure accurate and complete recording of all relevant transaction data.
Form and content should be kept as simple as possible to:
Promote efficient record keeping
Minimize recording errors
Facilitate review and verification
Documents that initiate a transaction should contain a space for authorization.
Those used to transfer assets should have a space for the receiving party’s signature.
CONTROL ACTIVITIES
Documents should be sequentially pre-numbered:
To reduce likelihood that they would be used fraudulently.
To help ensure that all valid transactions are recorded.
A good audit trail facilitates:
Tracing individual transactions through the system.
Correcting errors.
Verifying system output.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Safeguard Assets, Records, and Data
When people consider safeguarding assets, they most often think of cash and physical assets, such as inventory and equipment.
Another company asset that needs to be protected is information.
According to the ACFE’s 2004 National Fraud Survey, theft of information made up only 17.3% of non-cash misappropriations; however, the median cost of an information theft was $340,000. This cost was 126% higher than the next most costly non-asset theft. (Equipment theft had a median cost of $150,000.)
CONTROL ACTIVITIES
Many people mistakenly believe that the greatest risks companies face are from outsiders.
However, employees pose a much greater risk when it comes to loss of data because:
They know the system and its weaknesses better.
They are better able to hide their illegal acts.
CONTROL ACTIVITIES
Insiders also create less-intentional threats to systems, including:
Accidentally deleting company data
Turning viruses loose
Trying to fix hardware or software without appropriate expertise (i.e., when in doubt, unplug it).
These actions can result in crashed networks, corrupt data, and hardware and software malfunctions.
Companies also face significant risks from customers and vendors that have access to company data.
CONTROL ACTIVITIES
Many steps can be taken to safeguard both information and physical assets from theft, unauthorized use, and vandalism. Chapters 7 and 8 discuss computer-based controls. In addition, it is important to:
Maintain accurate records of all assets
Periodically reconcile recorded amounts to physical counts.
CONTROL ACTIVITIES
Many steps can be taken to safeguard both information and physical assets from theft, unauthorized use, and vandalism. Chapters 7 and 8 discuss computer-based controls. In addition, it is important to:
Maintain accurate records of all assets
Periodically reconcile recorded amounts to physical counts.
Restrict access to assets
Use restricted storage areas for inventories and equipment.
Use cash registers, safes, lockboxes, and safe deposit boxes to limit access to cash, securities, and paper assets.
CONTROL ACTIVITIES
Many steps can be taken to safeguard both information and physical assets from theft, unauthorized use, and vandalism. Chapters 7 and 8 discuss computer-based controls. In addition, it is important to:
Maintain accurate records of all assets
Periodically reconcile recorded amounts to physical counts.
Restrict access to assets
Protect records and documents
Use fireproof storage areas, locked filing cabinets, backup of files (including copies at off-site locations).
Limit access to blank checks and documents to authorized personnel.
CONTROL ACTIVITIES
Generally, control procedures fall into one of the following categories:
Proper authorization of transactions and activities
Segregation of duties
Project development and acquisition controls
Change management controls
Design and use of documents and records
Safeguard assets, records, and data
Independent checks on performance
CONTROL ACTIVITIES
Let’s look at Bill and Mary again. Assume that Bill stole cash but Mary did NOT alter the books.
Ledger $1,000
CONTROL ACTIVITIES
Can Bill’s theft be discovered if an independent party doesn’t compare a count of the cash to what’s recorded on the books?
Ledger $1,000
CONTROL ACTIVITIES
Segregation of duties only has value when supplemented by independent checks.
Ledger $1,000
CONTROL ACTIVITIES
Internal checks to ensure that transactions are processed accurately are an important control element.
These checks should be performed by someone independent of the party(ies) responsible for the activities.
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Management at all levels should monitor company results and periodically compare actual performance to:
Planned performance as shown in budgets, targets, and forecasts
Prior-period performance
The performance of competitors
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Analytical reviews
Examinations of relationships between different sets of data.
EXAMPLE: If credit sales increased significantly during the period and there were no changes in credit policy, then bad debt expense should probably have increased also.
Management should periodically analyze and review data relationships to detect fraud and other business problems.
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Analytical reviews
Reconciliation of independently maintained sets of records
Check the accuracy and completeness of records by reconciling them with other records that should have the same balance.
EXAMPLES:
Bank reconciliations
Comparing accounts payable control account to sum of subsidiary accounts.
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Analytical reviews
Reconciliation of independently maintained sets of records
Comparison of actual quantities with recorded amounts
Periodically count significant assets and reconcile the count to company records.
EXAMPLE: Annual physical inventory.
High-dollar items and critical components should be counted more frequently.
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Analytical reviews
Reconciliation of independently maintained sets of records
Comparison of actual quantities with recorded amounts
Double-entry accounting
Ensure that debits equal credits.
CONTROL ACTIVITIES
The following independent checks are typically used:
Top-level reviews
Analytical reviews
Reconciliation of independently maintained sets of records
Comparison of actual quantities with recorded amounts
Double-entry accounting
Independent review
After one person processes a transaction, another reviews their work.
INFORMATION AND COMMUNICATION
The seventh component of COSO’s ERM model.
The primary purpose of the AIS is to gather, record, process, store, summarize, and communicate information about an organization.
So accountants must understand how:
Transactions are initiated
Data are captured in or converted to machine-readable form
Computer files are accessed and updated
Data are processed
Information is reported to internal and external parties
INFORMATION AND COMMUNICATION
Accountants must also understand the accounting records and procedures, supporting documents, and specific financial statement accounts involved in processing and reporting transactions.
The preceding items facilitate an audit trail which allows for transactions to be traced from origin to financial statements and vice versa.
INFORMATION AND COMMUNICATION
According to the AICPA, an AIS has five primary objectives:
Identify and record all valid transactions.
Properly classify transactions.
Record transactions at their proper monetary value.
Record transactions in the proper accounting period.
Properly present transactions and related disclosures in the financial statements.
INFORMATION AND COMMUNICATION
Accounting systems generally consist of several accounting subsystems, each designed to process transactions of a particular type.
Though they differ with respect to the type of transactions processed, all accounting subsystems follow the same sequence of procedures, referred to as accounting cycles .
The five major accounting cycles and their related control objectives and procedures are detailed in Chapters 10-14.
MONITORING
The eighth component of COSO’s ERM model.
Monitoring can be accomplished with a series of ongoing events or by separate evaluations.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Perform ERM Evaluation
Can measure ERM effectiveness through a formal evaluation or through a self-assessment process.
A special group can be assembled to conduct the evaluation or it can be done by internal auditing.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Implement Effective Supervision
Involves:
Training and assisting employees;
Monitoring their performance;
Correcting errors; and
Safeguarding assets by overseeing employees with access.
Especially important in organizations that:
Can’t afford elaborate responsibility reporting; or
Are too small for segregation of duties.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Use Responsibility Accounting
Includes use of:
Budgets, quotas, schedules, standard costs, and quality standards;
Performance reports that compare actual with planned performance and highlight variances;
Procedures for investigating significant variances and taking timely actions to correct adverse conditions.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Monitor System Activities
Risk analysis and management software packages are available to:
Review computer and network security measures;
Detect illegal entry into systems;
Test for weaknesses and vulnerabilities;
Report weaknesses found; and
Suggest improvements.
MONITORING
Cost parameters can be entered to balance acceptable levels of risk tolerance and cost-effectiveness.
Software is also available to monitor and combat viruses, spyware, spam, pop-up ads, and to prevent browsers from being hijacked.
Also helps companies recover from frauds and malicious actions and restore systems to pre-incident status.
MONITORING
System transactions and activities should be recorded in a log which indicates who accessed what data, when, and from which terminal.
Logs should be reviewed frequently to monitor system activity and trace any problems to their source.
Data collected can be used to:
Evaluate employee productivity;
Control company costs;
Fight corporate espionage and other attacks; and
Comply with legal requirements.
MONITORING
Companies that monitor system activities need to ensure they do not violate employee privacy rights.
Employers cannot discreetly observe communications of employees when those employees have a “reasonable expectation of privacy.”
Employers must therefore ensure that employees realize their business communications are not “private.” One way to accomplish that objective is to have written policies that employees agree to in writing which indicate:
The technology employees use on the job belongs to the company.
Emails received on company computers are not private and can be read by supervisory personnel.
Employees should not use technology in any way to contribute to a hostile work environment.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Track Purchased Software
The Business Software Alliance (BSA) aggressively tracks down and fines companies who violate software license agreements.
To comply with copyrights, companies should periodically conduct software audits to ensure that.
There are enough licenses for all users;
The company is not paying for more licenses than needed.
Employees should be informed of the consequences of using unlicensed software.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Conduct Periodic Audits
To monitor risk and detect fraud and errors, the company should have periodic:
External audits
Internal audits
Special network security audits
Auditors should test system controls and browse system usage files looking for suspicious activities (discussed in Chapter 9).
MONITORING
Again, care should be exercised that employees’ privacy rights are not violated.
Therefore, inform employees that auditors will conduct random surveillance, which:
Avoids privacy violations
Creates a “perception of detection” that can deter crime and reduce errors
MONITORING
Internal auditing involves:
Reviewing the reliability and integrity of financial and operating information.
Providing an appraisal of internal control effectiveness.
Assessing employee compliance with management policies and procedures and applicable laws and regulations.
Evaluating the efficiency and effectiveness of management.
MONITORING
Internal audits can detect:
Excess overtime
Under-used assets
Obsolete inventory
Padded expense reimbursements
Excessively loose budgets and quotas
Poorly justified capital expenditures
Production bottlenecks
MONITORING
Internal auditing should be organizationally independent of the accounting and operating functions.
The head should report to the audit committee of the board of directors rather than to the controller or CFO.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Employ a Computer Security Officer and Computer Consultants
The computer security officer (CSO) is in charge of AIS security
Should be independent of the IS function
Should report to the COO or CEO
Many companies also use outside computer consultants or in-house teams to test and evaluate their security procedures and computer systems.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Engage Forensic Specialists
Forensic accountants specialize in fraud detection and investigation.
Now one of the fastest growing areas of accounting due to:
SOX
SAS-99
Boards of Directors demanding that forensic accounting be an ongoing part of the financial reporting and corporate governance process.
MONITORING
Most forensic accountants are CPAs and may have received special training with the FBI, CIA, or other law enforcement agencies.
In particular demand are those with the necessary computer skills to ferret out and combat fraudsters who use sophisticated technology to perpetrate their crimes.
The Association of Certified Fraud Examiners (ACFE) has created a professional certification program for fraud examiners.
Most forensic accountants are CPAs and may have received special training with the FBI, CIA, or other law enforcement agencies.
MONITORING
Management may also need to call on computer forensic specialists for help.
They assist in discovering, extracting, safeguarding, and documenting computer evidence so that its authenticity, accuracy, and integrity will not succumb to legal challenges.
MONITORING
Common incidents investigated by computer forensic experts include:
Improper internet usage
Fraud
Sabotage
Loss, theft, or corruption of data
Retrieving information from emails and databases that users thought they had erased
Determining who performed certain actions on a computer
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Install Fraud Detection Software
People who commit fraud tend to follow certain patterns and leave behind clues.
Software has been developed to seek out these fraud symptoms.
Some companies employ neural networks (programs that mimic the brain and have learning capabilities) which are very accurate in identifying suspected fraud.
For example, if a husband and wife were each using the same credit card in two different stores at the same time, a neural network would probably flag at least one of the transactions immediately as suspicious.
These networks and other recent advances in fraud detection software are significantly reducing the incidences of credit card fraud.
MONITORING
Key methods of monitoring performance include:
Perform ERM evaluation
Implement effective supervision
Use responsibility accounting
Monitor system activities
Track purchased software
Conduct periodic audits
Employ a computer security officer and security consultants
Engage forensic specialists
Install fraud detection software
Implement a fraud hotline
MONITORING
Implement a Fraud Hotline
People who witness fraudulent behavior are often torn between conflicting feelings.
They want to protect company assets and report fraud perpetrators.
But they are uncomfortable in the whistleblower role and find it easier to remain silent.
They are particularly reluctant to report if they know of others who have suffered repercussions from doing so.
MONITORING
SOX mandates that companies set up mechanisms for employees to anonymously report abuses such as fraud.
An effective way to comply with the law and resolve employee concerns is to provide access to an anonymous hotline.
Anonymous reporting can be accomplished through:
Phone lines
Web-based reporting
Anonymous emails
Snail mail
MONITORING
Outsourcing is available through a number of third parties and offers several benefits, including:
Increased confidence on the part of employee that his/her report is truly anonymous.
24/7 availability.
Often have multilingual capabilities—an important plus for multinational organizations.
The outsourcer may be able to do follow up with the employee if additional information is needed after the initial contact.
The employee can be advised of the outcome of his report.
Low cost.
MONITORING
A downside to anonymous reporting mechanisms is that they will produce a significant amount of petty or slanderous reports that do not require investigation.
The ACFE’s 2004 Report to the Nation indicates that companies without fraud hotlines had median fraud losses that were 140% higher than companies that had fraud hotlines.
SUMMARY
In this chapter, you’ve learned about basic internal control concepts and why computer control and security are so important.
You’ve learned about the similarities and differences between the COBIT, COSO, and ERM control frameworks.
You’ve learned about the major elements in the internal control environment of a company and the four types of control objectives that companies need to set.
You’ve also learned about events that affect uncertainty and how these events can be identified.
You’ve explored how the Enterprise Risk Management model is used to assess and respond to risk, as well as the control activities that are commonly used in companies.
Finally, you’ve learned how organizations communicate information and monitor control processes.